Home > Elements Public APIs > Get the Access Token
Export to PDFGet the Access Token
Based on the credentials of an app registration in Elements, refer to the following sections:
Client Secret
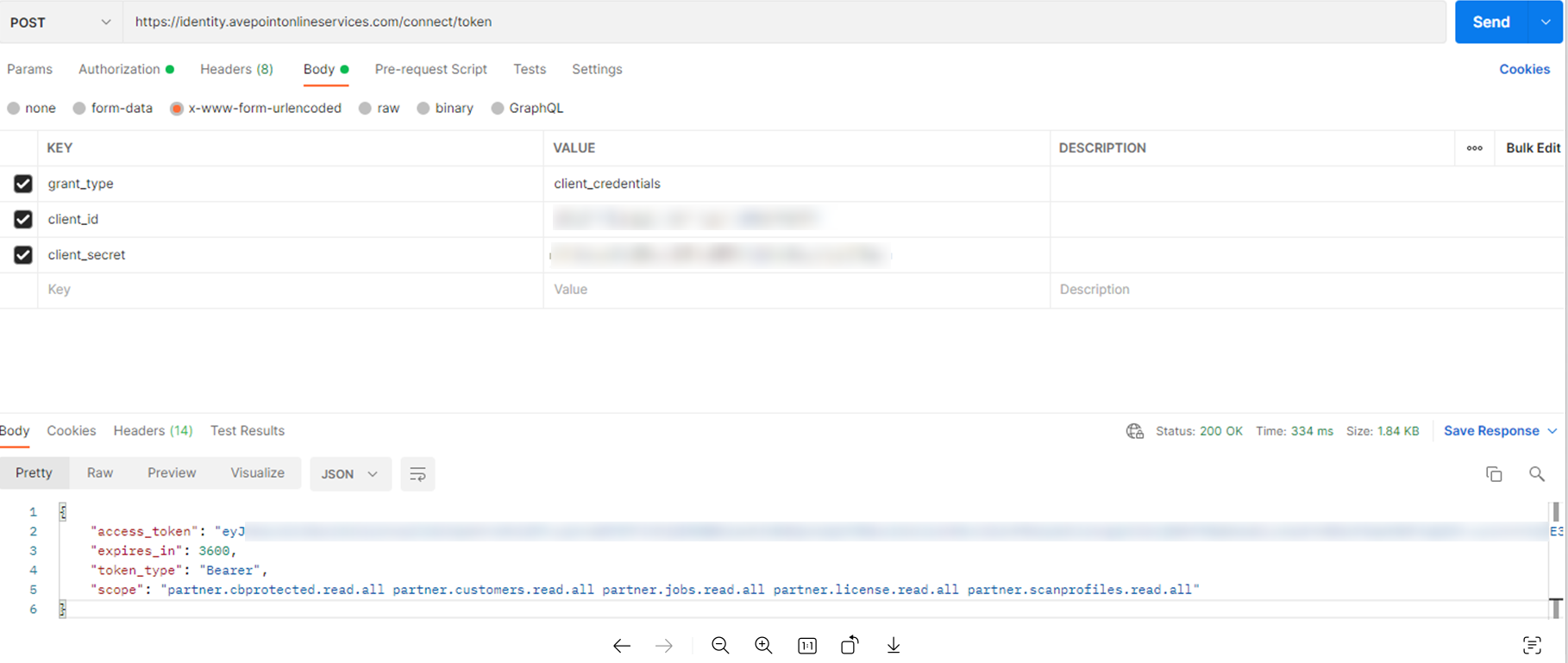
If you want to get the access token with a client secret in an app registration, follow the instructions below to send a POST request:
-
Set the access token URL: https://identity.avepointonlineservices.com/connect/token.
-
Set the header to Content-Type: application/x-www-form-urlencoded.
-
Set the following parameters in the request body:
-
client_id – Copy the Application (Client) ID value in the app registration and paste the value here.
-
client_secret – Copy the Client Secret value that has been saved upon the creation of the app registration, and paste the value here.
-
scope – Set the scope, which is the assigned permissions. Please ensure the permissions have been configured in the app registration.
-
grant_type – Set this value to client_credentials.
-
-
In the response, the access_token node represents the token value, the expires_in node represents the token will expire in how many seconds, and the scope node lists the assigned permissions of the app registration.
You can use Postman to test the POST request as below:
Certificate
Once you have the application (client) ID, get the access token via the application (client) ID to authenticate with Elements APIs.
The following information is required to get an access token:
| Element | Description |
|---|---|
| Identity Service URL | https://identity.avepointonlineservices.com |
| Application (Client) ID | The application (client) ID you have retrieved. |
| Certificate | The corresponding .pfx certificate file of the .cer certificate you used when registering the app. |
To get the access token using the above information, create a JSON web token using the Client ID and certificate first, and then use the JSON web token to request an access token of the defined scope from Identity Service.
Below is an example for getting the access token.
The token you get will expire in one hour, and you need to get the token again after the expiration.
