Home > Perform Gmail Migrations > Required Permissions for Gmail Migration > Permissions for Destination Exchange Online
Export to PDFPermissions for Destination Exchange Online
To connect to the destination, you can choose to only use a service account, Fly app profile, or custom app profile as the authentication method. You can also use the combination of a service account and a Fly app profile, or the combination of a service account and a custom app profile.
Refer to the following sections to view the permissions required by the authentication methods.
Fly App Profile Permissions
With the Tenant Owner or Service Administrator role, you can create a Fly app profile in AvePoint Online Services > Management > App management to connect to the Microsoft 365 tenant using the Fly app.
Refer to Fly App Profile Permissions about how to create a Fly app profile and required permissions of the Fly app profile.
If you want to perform Exchange Online tenant discovery or Exchange Online to Exchange Online migrations, make sure the account that authorizes the app has a mailbox (either by assigning the Exchange license or using PowerShell to create a mailbox).
You need to assign the Exchange Administrator role to the AvePoint Fly app in the following situations. Refer to How to Assign the Exchange Administrator Role to an App? for instructions.
If you do not want to assign the Exchange administrator role to the app authorization user, you can add custom roles to the app to ensure the availability of above functions. Refer to How to Add Custom Roles to an App? for details.
Custom App Profile Permissions
With the Tenant Owner and Service Administrator role, you can create a custom app profile in AvePoint Online Services > Management > App management to connect to the Microsoft 365 tenant using a custom Azure app.
Refer to the following procedures to create a custom app profile:
-
Prepare a certificate in Microsoft Entra ID. Refer to for more information.
You can ignore this step if you have a certificate.
-
Create a custom Azure app in Microsoft Entra ID. Refer to for more information.
-
.
-
in AvePoint Online Services.
After you re-authorize the app profile, you need to wait about one hour before using the app profile for your migration to refresh the token if there are permissions updated.
Refer to the following tables to add API permissions required by Exchange Online.
Note the following:
| API | Permission | Type | Purpose |
|---|---|---|---|
| Office 365 Exchange Online | full_access_as_app(Use Exchange Web Services with full access to all mailboxes) | Application | Retrieve and migrate items from all mailboxes.*Note: If you do not want to add this permission to the app, you can create an RBAC assignment for the app to only access to specified mailboxes. Refer to the option 3 in the How to Migrate Mailboxes without the ApplicationImpersonation Role? section for details. |
| Office 365 Exchange Online | Exchange.ManageAsApp(Manage Exchange As Application) | Application | Migrate Google groups and mailbox aliases. |
| Microsoft Graph | User.Read.All(Read and write all users’ full profiles) | Application | Retrieve the information of Microsoft 365 user profiles. |
| Microsoft Graph | Calendars.ReadWrite(Read and write calendars in all mailboxes) | Application | Required if you want to keep the source Response statuses of event attendees to the destination. |
| Microsoft Graph | Group.ReadWrite.All(Read and write all groups) | Application | Required when you do not assign the Exchange Administrator role to the app. Retrieve Microsoft 365 Group mailboxes and mailbox types, and create Microsoft 365 Group mailboxes in the destination. |
For easy use, you can directly use the following commands to add required API permissions through Manifest for Microsoft 365 Commercial tenants.
"requiredResourceAccess": [
{
"resourceAppId": "00000003-0000-0000-c000-000000000000",
"resourceAccess": [
{
"id": "62a82d76-70ea-41e2-9197-370581804d09",
"type": "Role"
},
{
"id": "df021288-bdef-4463-88db-98f22de89214",
"type": "Role"
},
{
"id": "ef54d2bf-783f-4e0f-bca1-3210c0444d99",
"type": "Role"
}
]
},
{
"resourceAppId": "00000002-0000-0ff1-ce00-000000000000",
"resourceAccess": [
{
"id": "dc890d15-9560-4a4c-9b7f-a736ec74ec40",
"type": "Role"
},
{
"id": "dc50a0fb-09a3-484d-be87-e023b12c6440",
"type": "Role"
}
]
}
],
Service Account Permissions
The Tenant Owner and Service Administrators can also for Microsoft 365 to connect AvePoint Online Services to your Microsoft 365 tenant.
Users with Multi-Factor Authentication (MFA) enabled cannot be used as the service account to perform migrations. You can use a delegated app profile instead.
Make sure the service account has a mailbox (either by assigning the Exchange license or using PowerShell to create a mailbox) and meets the following requirements:
To make sure the source service account has a mailbox, go to the Microsoft 365 admin center > Users > Active users, and select Exchange Online under the Licenses and apps tab of the service account.
| Required Permission | Note |
|---|---|
| ApplicationImpersonation role or Full Access permission to destination mailboxes in the migration | Microsoft has announced the retirement of the ApplicationImpersonation role in Exchange Online. Refer to Impact and Solutions for the Retirement of the ApplicationImpersonation Role in Exchange Online for details.If you do not migrate Google groups in the migration, you can grant the Full Access permission without adding the ApplicationImpersonation role. |
| Mail Recipients role | Retrieve mailboxes when performing Gmail migrations. |
| Mail Recipient Creation role | Required if you want to create shared mailboxes and resource mailboxes in the destination. |
| Distribution Groups role | Required if you want to migrate Google groups to distribution groups. |
| Security Group Creation and Membership role | Required if you want to migrate Google groups to mail-enabled security groups. If the service account is the Exchange Administrator, this role is not required. |
| Groups administrator role in the admin centers | Required if you want to migrate Google groups to existing Microsoft 365 Groups. |
What permissions are required if I also use an app profile?
If you use both service account and app profile authentications for the destination Exchange Online, and the app profile has the Exchange Administrator role, there are no permission requirements for the service account. If the app profile does not have the Exchange Administrator role, some service account permissions will not be required and you need to make sure the service account has a mailbox and the following permissions:
To make sure the destination service account has a mailbox, go to the Microsoft 365 admin center > Users > Active users, and select Exchange Online under the Licenses and apps tab of the service account.
| Destination Service Account Permissions | Note |
|---|---|
| Mail Recipients role | Retrieve mailboxes when performing Gmail migrations. |
| Mail Recipient Creation role | Required if you want to create shared mailboxes and resource mailboxes in the destination. |
| Distribution Groups role | Required if you want to migrate Google groups to distribution groups. |
| Security Group Creation and Membership role | Required if you want to migrate Google groups to mail-enabled security groups. |
Delegated App Profile Permissions
Fly allows you to use the Fly delegated app profile or custom delegated app profile to connect to your workspace.
To use a delegated app profile, note the following:
To use the Fly delegated app profile with required permissions, refer to Fly Delegated App Profile Permissions.
To use a custom delegated app profile with required permissions, refer to the following steps:
- After registering an app in Microsoft Entra ID, add the permissions in the table below to the app.
| API | Permission | Type | Purpose |
|---|---|---|---|
| Office 365 Exchange Online | EWS.AccessAsUser.All(Access mailboxes as the signed-in user via Exchange Web Services) | Delegated | Access specified user and import data. |
| Office 365 Exchange Online | Exchange.Manage(Manage Exchange configuration) | Delegated | Use Exchange PowerShell to migrate mailbox permissions, distribution lists, and dynamic distribution lists. |
| Microsoft Graph | Domain.Read.All(Read domains) | Delegated | Create Microsoft 365 Group mailboxes. |
| Microsoft Graph | Group.ReadWrite.All(Read and write all groups) | Delegated | Create Microsoft 365 Group mailboxes. |
"requiredResourceAccess": [
{
"resourceAppId": "00000003-0000-0000-c000-000000000000",
"resourceAccess": [
{
"id": "2f9ee017-59c1-4f1d-9472-bd5529a7b311",
"type": "Scope"
},
{
"id": "4e46008b-f24c-477d-8fff-7bb4ec7aafe0",
"type": "Scope"
}
]
},
{
"resourceAppId": "00000002-0000-0ff1-ce00-000000000000",
"resourceAccess": [
{
"id": "ab4f2b77-0b06-4fc1-a9de-02113fc2ab7c",
"type": "Scope"
},
{
"id": "3b5f3d61-589b-4a3c-a359-5dd4b5ee5bd5",
"type": "Scope"
}
]
}
],
-
Click Authentication in the left navigation of the app.
-
Click Add a platform.
-
Select Web in the Configure platforms panel.
-
In the Configure Web panel, enter the AvePoint Online Services URL: https://www.avepointonlineservices.com for your commercial environment or https://usgov.avepointonlineservices.com for your U.S. Government environment in the Redirect URIs field.
-
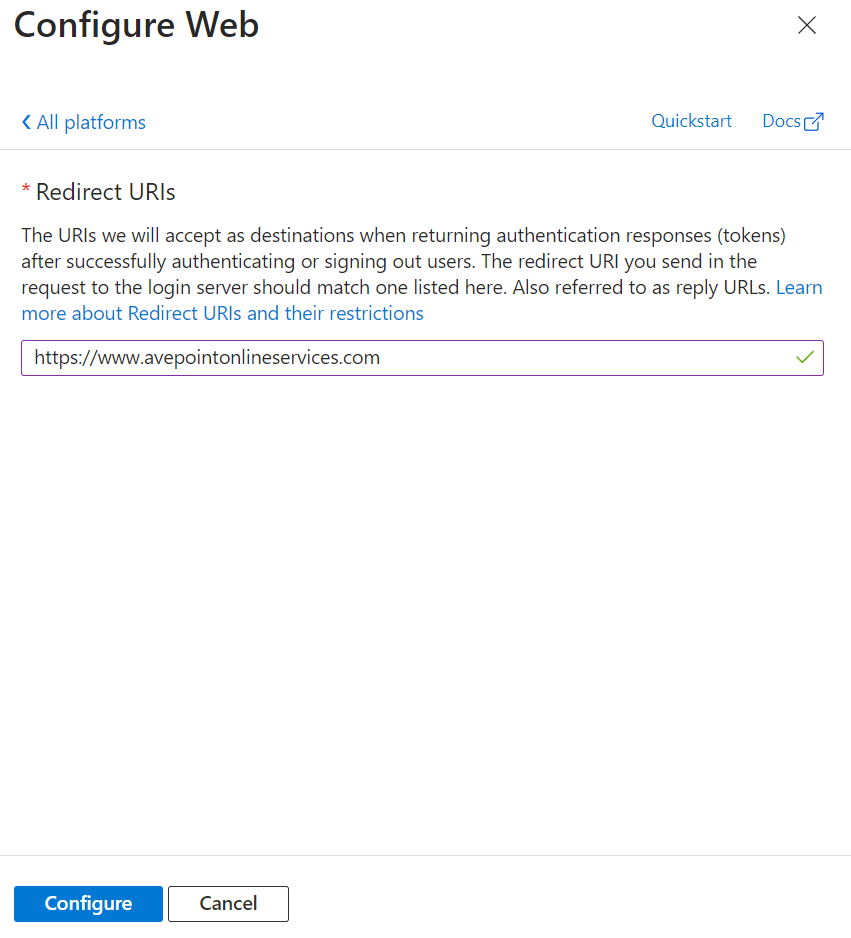
-
Click Configure.
-
Select the Access tokens and ID tokens checkboxes on the Authentication page.
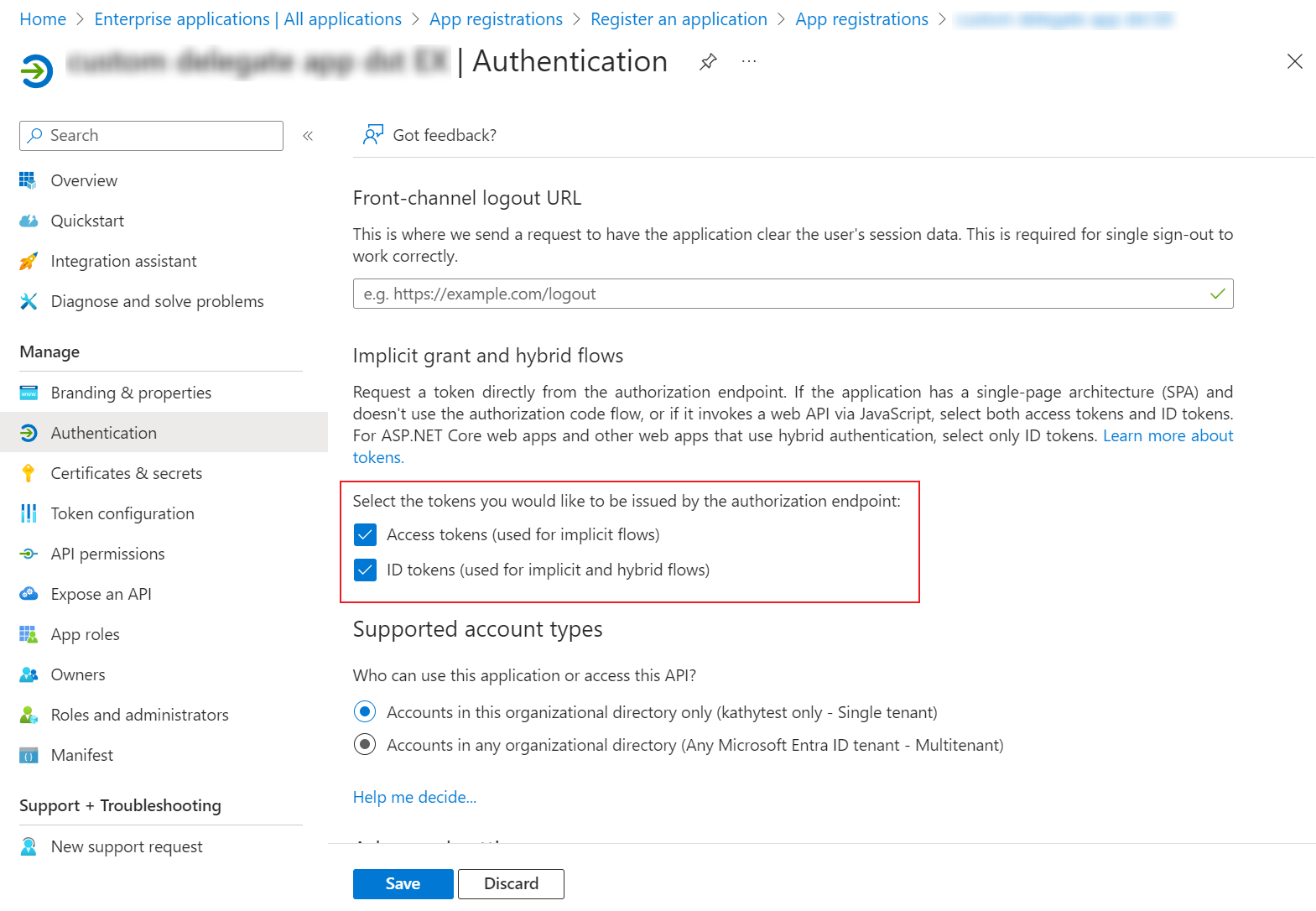
-
Click Save.
-
Create an app profile for the app using the Custom mode in AvePoint Online Services by referring to .
-
*Note: When consenting to the app, if you have granted the admin consent and allowed public client flows for the permissions, you can choose to use the Global Administrator consent or the User consent method. If not, you can only use the Global Administrator consent method.
