Home > Perform Active Directory Migrations > Create a Connection
Export to PDFCreate a Connection
To connect Fly to your source or destination Active Directory for an Active Directory to Active Directory Migration, you need to add Active Directory connections by completing the following steps.
-
Click Settings in the left pane, and select Connections to access the Connections page.
-
Click Create connection. The Create connection panel appears.
-
In the Create connection panel, complete the following settings:
-
Connection name – Enter a name for the connection.
-
Connection type – Select Active Directory from the drop-down list to create a connection for Active Directory.
-
Configure source or destination connection – Select Source or Destination to define if the connection is used as the source or destination.
-
SQL database – Configure the Azure SQL database to store source Active Directory objects based on your needs.
-
Custom Azure SQL database – Enter the connection string of the custom Azure SQL database. For how to find the connection string, refer to .
-
If your organization has an access policy and only specific IP addresses are allowed, you need to navigate to AvePoint Online Services > Administration > Security > Reserved IP addresses to download the list of reserved IP addresses required by AvePoint Online Services and Fly. Then, add the IP addresses to the server-level and/or database-level IP firewall rule lists in Microsoft Azure. If you do not want to add the IP addresses, you can also select the Allow Azure services and resources to access this server checkbox under the server-level and/or database-level IP firewall rule lists to allow connections from IP addresses allocated to any Azure service or asset.
-
Default Azure SQL database – Use the default Azure SQL database that is provided by Microsoft for Active Directory migrations.
-
-
Generate connection key – Click Generate to generate a connection key. The key will be used to connect the Active Directory agent. You can click the Copy button to copy the key.
-
Download and install Active Directory agent – Click Download source agent/Download destination agent based on your configurations to download the agent and install it on the source/destination Active Directory server. Refer to Install the Active Directory Agent for how to install the agent. If the agent cannot be installed on the source/destination Active Directory server due to security configurations, install the agent on a server that can connect to the source/destination Active Directory.
-
-
Click Save to save your configurations.
On the Connections page, you can manage the existing connections.
Install the Active Directory Migration Agent
Refer to the following sections to prepare and install the Active Directory migration agent.
System Requirements
Refer to the following table for the system requirements of the Fly Active Directory Migration Agent.
| Components | Requirements |
|---|---|
| Operating System | Windows Server 2016, Windows Server 2019, Windows Server 2022, Windows 10, Windows 11*Note: 32-bit operating systems are not supported. Only operating systems with Desktop Experience are supported. |
| Number of CPU Cores | Recommended: 4 or above. |
| Available Physical Memory | Recommended: 8 GB or above. |
| Available Disk Space | The Agent server will store the temporary files and job logs of migrations. ● We recommend 50 GB or above for migration projects with less than 100 GB of data.● We recommend 100 GB or above for large migration projects with more than 200 GB of data.When checking the installation rules, Fly checks the storage space of your drive C by default. Make sure there is available space of 2 GB or above in your drive C. |
| .NET Framework Version | .NET Framework 4.7.2 to 4.8. |
| Net.Tcp Port Sharing Service | Net.Tcp Port Sharing Service has started. |
| Transport Layer Security (TLS) Version | TLS 1.2 is enabled. |
| Visual C++ Redistributable Version | Visual C++ Redistributable 2015-2022. |
System Services Port Requirements
Refer to the following information for the system services port requirements of the Fly Active Directory Migration Agent.
| Application Protocol | Protocol | Ports |
|---|---|---|
| Lightweight Directory Access Protocol (LDAP) Server | TCP | 389 |
| Remote Procedure Call (RPC) | TCP | 135 |
| RPC randomly allocated high TCP ports | TCP | 49125 - 65535 |
For more details, refer to .
Network Requirements
Before performing Active Directory migrations in Fly, make sure the network of the server where you want to install the Active Directory agent can connect to the AvePoint Online Services, Fly, and the source/destination Active Directory.
If your organization has an access policy and only specific IP addresses are allowed, you need to navigate to AvePoint Online Services > Administration > Security > Reserved IP addresses to download the list of reserved IP addresses required by AvePoint Online Services and Fly, and then add the IP addresses to the safe IP address list of the server where you want to install the Active Directory agent.
Permission Requirements
Before performing Active Directory migrations in Fly, prepare the following accounts for the migration:
Download Agent
You can either download the Active Directory agent when creating a connection for Active Directory migration or follow the steps below to download the agent:
-
Click Settings in the left pane, and select Agents > Active Directory agent tab.
-
Click the down arrow next to Download agent, and then click Download source agent or Download destination agent to download the corresponding agent.
-
In the panel, click Download.
-
To verify whether a downloaded package has been tampered with, check its hash value and compare it with the one displayed in the panel. Following the steps below to obtain the hash value from the package:
-
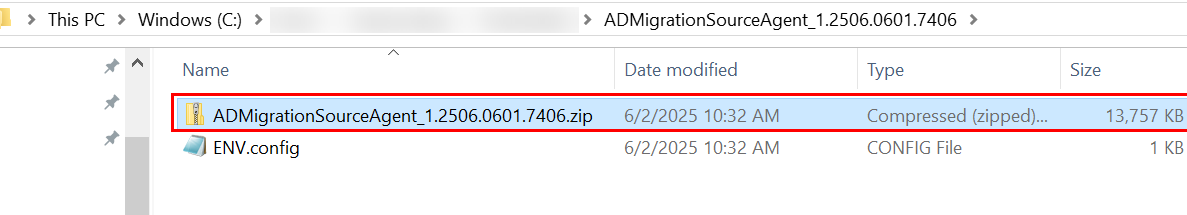
Extract the downloaded agent package.
-
Open Windows PowerShell and enter the following commands:
-
Get-FileHash -Algorithm SHA256 -Path “[file path]”
Replace [file path] with the full path of the ZIP file in the extracted package.
-
-
Install the Source Agent
Refer to the following steps to install the source Active Directory agent:
-
Copy the downloaded ZIP file of the source agent to the machine where you want to install the agent.
-
Extract the file.
-
Right-click the Setup.exe application file in the extracted folder, and select Run as administrator.
-
On the installation wizard, configure the installation path and click Next.
-
Fly will perform a brief pre-scan of the environment to ensure that all rules meet the requirements. The status for each rule will be listed in the Status column.

6. Click Next to install the agent. When the installation is finished, click Configure now to configure settings for the agent.
7. In the Connect AvePoint Online Services step, configure the following settings:
8. Click Next to go to the Connect Connection step.
-
In the Connect Connection step, configure the following settings:
-
Connection key – Paste the connection key you copied when you create the connection.
-
Connection name – After you entered the API key, the name of connection you created will be automatically filled in and cannot be edited.
-
Shared key – Enter 6 to 15 characters as the shared key. This key is used to encrypt Active Directory user passwords before sending them to the Fly database for migration. You need to save the shared key and provide the identical one to the destination agent for decryption.
NOTEWe recommend that you connect only one Active Directory agent per connection.
-
-
Click Next to go to the Connect Active Directory step.
-
In the Connect Active Directory step, configure the following settings:
-
Active Directory server information – Enter the host or IP: port of the source Active Directory.
-
Domain – Click Connect to retrieve the domain name of the source Active Directory.
-
Service account – Enter the account of a domain admin of the source Active Directory.
-
Password – Enter the password for the account specified above.
-
-
Click Next to go to the Scan Source Objects step.
-
In the Scan Source Objects step, select the OUs you want to scan. You can also enter the OU name in the search box to search for the OU.
-
Click Next to go to the Scan Schedule step.
-
In the Scan Schedule step, configure the following settings:
-
Scan security properties:
-
User passwords – Select this to scan and migrate the user passwords. Note that the Remote Procedure Call (RPC) server must be available for this migration.
-
Security Identifier (SID) History – Select this to scan and migrate the Security Identifier (SID) History. Note that the Remote Procedure Call (RPC) server must be available for this migration. Before performing the SID History migration, refer to the Prepare for SID History Migration section for detailed preparation steps.
-
-
Scan method:
-
Scan and send now – Select this to scan source objects and send the scanned objects to Fly immediately.
-
Scan on a specific date and time – Configure the start and end date and time, and the interval of recurring jobs.
-
-
-
Click Submit to save your configurations.
If the agent is installed on a domain controller machine, ensure you run the agent as an administrator.
Install the Destination Agent
Refer to the following steps to install the destination Active Directory agent:
-
Copy the downloaded ZIP file of the destination agent to the machine where you want to install the agent.
-
Extract the file.
-
Right-click the Setup.exe application file in the extracted folder, and select Run as administrator.
-
On the installation wizard, configure the installation path and click Next.
-
Fly will perform a brief pre-scan of the environment to ensure that all rules meet the requirements. The status for each rule will be listed in the Status column.

6. Click Next to install the agent. When the installation is finished, click Configure now to configure settings for the agent.
-
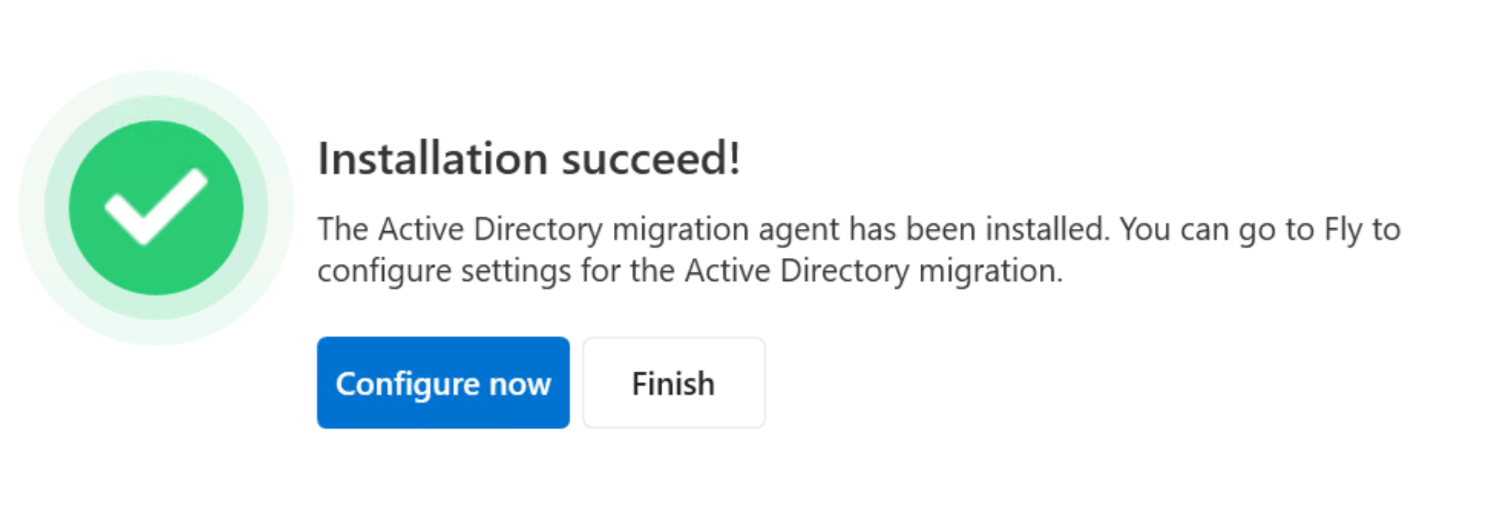
-
In the Connect AvePoint Online Services step, configure the following settings:
-
*Note: The same app registration can be used for both source and destination agents.
-
AvePoint Online Services application (client) ID – Enter the ID of your app registration in AOS > Administration > App registrations. Note that the fly.admigration.readwrite.all permission is required for this app registration.
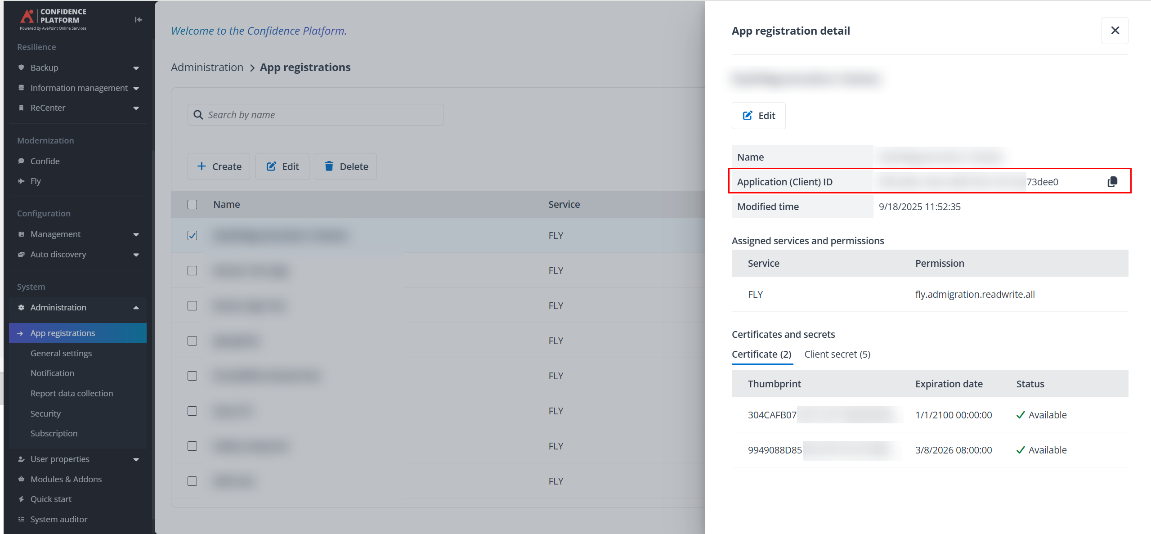
-
Certificates – Configure the certificate thumbprint in AOS > Administration > App registrations. For how to upload a new certificate, refer to the Register an App section in for detailed information.
-
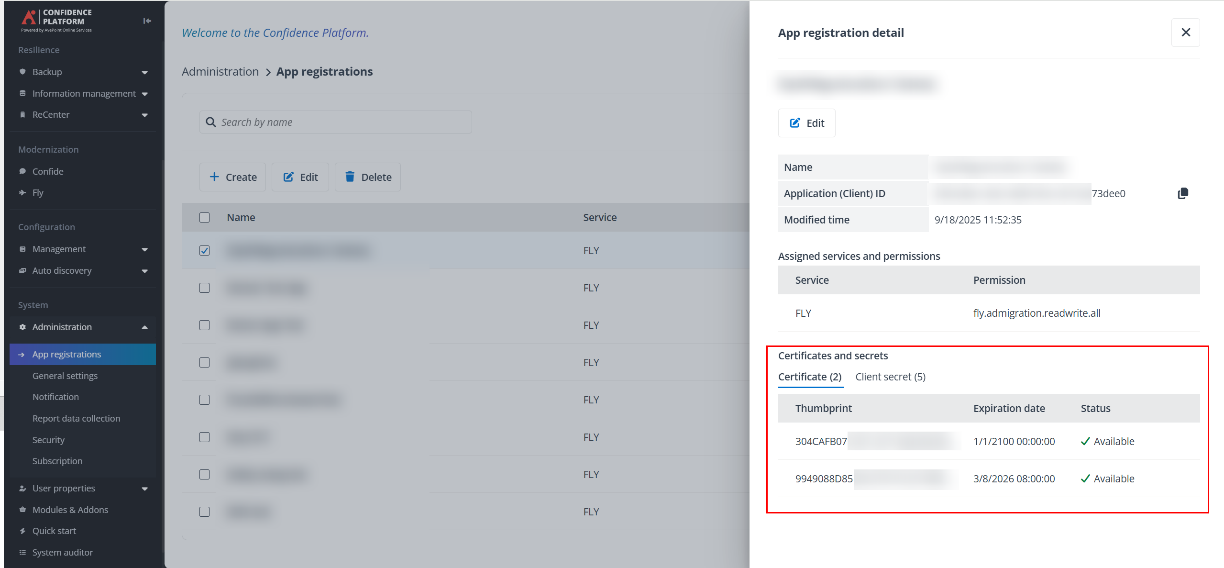
-
Note the following:
-
Client secrets are not required for the connection.
-
The certificate (.pfx) must be installed on the Local Machine that has destination Active Directory agent installed.
-
You can choose to create a new certificate for the destination agent or use the same one as the source agent. In either case, the certificate (.pfx) must be installed on the Local machine that has destination Active Directory agent installed.
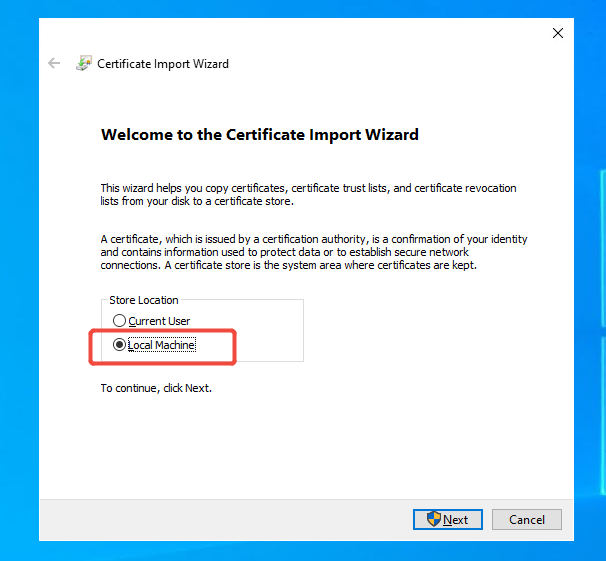
-
-
Proxy settings – Configure the following settings:
-
Proxy Host – The hostname or IP address of the proxy server.
-
Proxy Port – The port used to access the proxy server.
-
Username – The username to log in to the proxy server.
-
Password – The password to access the proxy server.
-
-
-
Click Next to go to the Connect Connection step.
-
In the Connect Connection step, configure the following settings:
-
Connection key – Paste the connection key you copied when you create the connection.
-
Connection name – After you entered the API key, the name of connection you created will be automatically filled in and cannot be edited.
-
Shared key – Enter the same shared key configured in the source agent. It is required to decrypt passwords while syncing the passwords for destination Active Directory users.
NOTEWe recommend that you connect only one Active Directory agent per connection.
-
-
Click Next to go to the Connect Active Directory step.
-
In the Connect Active Directory step, configure the following settings:
-
Active Directory server information – Enter the host or IP: port of the destination Active Directory.
-
Domain – Click Connect to retrieve the domain name of the destination Active Directory.
-
Service account – Enter an account that is both a domain admin and a schema admin of the destination Active Directory.
-
Password – Enter the password for the account specified above.
NOTEAfter the destination Active Directory is connected to Fly, a new attribute named flymigrationExtensionAttribute will be created in the destination Active Directory.
-
-
Click Next to go to the Advanced settings step.
-
In the Advanced settings step, you can turn on the toggle to enable the Security Identifier (SID) History migration if required. Note that before performing the SID History migration, refer to the Prepare for SID History Migration section for detailed preparation steps.
-
Once enabled, configure the following settings:
-
Source Active Directory server – Enter the host or IP: port of the source Active Directory.
-
Domain – Click Connect to retrieve the domain name of the source Active Directory.
-
Service account – Enter the account of a domain admin of the source Active Directory.
-
Password – Enter the password for the account specified above.
-
-
Click Next to go to the Import Objects step.
-
In the Import Objects step, configure the interval time for importing objects from Fly to the destination agent. The unit is Second.
-
Click Finish to finish the installation of the destination agent.
If the agent is installed on a domain controller machine, ensure you run the agent as an administrator.
Prepare for SID History Migration
Before performing the Security Identifier (SID) History migration, you need to complete the following steps to prepare for the migration:
-
Create a local group in the source domain:
-
Open Active Directory Users and Computers.
-
Locate and right-click the required OU and select New > Group.
-
In the New Object - Group window, enter the group name using the following format: <source domain’s NetBIOS name>$$$.
For example, if the NetBIOS name of your source domain is FLY, the group name must be FLY$$$.
You can run the following commands in PowerShell to retrieve the BIOS name of your source domain: (Get-ADDomain).NetBIOSName.
NOTEThe SID History migration will fail if members are added to this newly created local group.
-
-
Enable TCP/IP client support on the source domain PDC emulator:
-
On the domain controller in the source domain that holds the PDC emulator operations master (also known as Flexible Single Master Operations or FSMO) role, navigate to Start menu> Run.
-
In the Run window, enter regedit in the Open field, then click OK.
-
-
In the Registry Editor window, Go to the following registry key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA
-
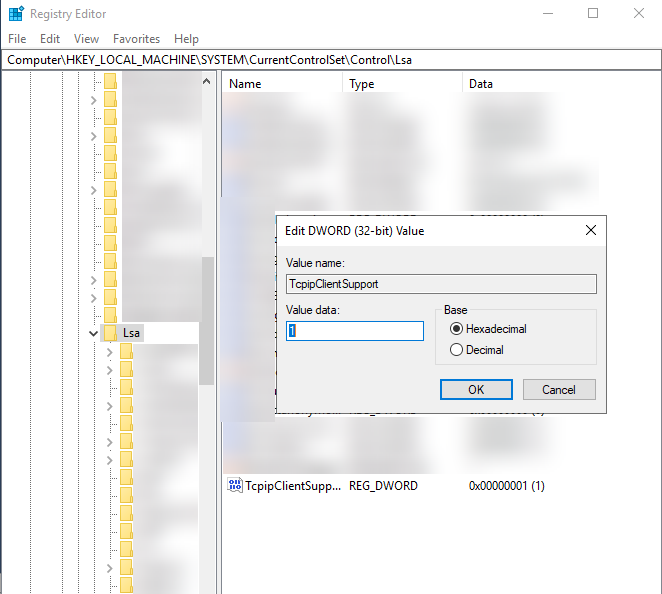
Locate the TcpipClientSupport registry entry (type: REG_DWORD). Right-click it and select Modify....
-
In the Edit DWORD (32-bit) Value window, enter 1 in the Value data field.
-
-
Click OK.
-
Close Registry Editor window and restart the computer for the change to take effect.
-
-
Log on as an administrator to any domain controller in the destination/source domain.
-
Navigate to Start menu > Administrative Tools > Group Policy Management.
-
In the Group Policy Management window, navigate to Forest > Domains > Domain Name > Domain Controllers > Default Domain Controllers Policy.
-
Right-click the Default Domain Controllers Policy, and click Edit. The Group Policy Management Editor window appears.
NOTEIf you cannot edit the policy, you can try to re-open the Group Policy Management Editor window by navigating to Start menu> Run. In the Run window, enter gpmc.msc in the Open field, then click OK.
-
Enable auditing in the destination and source domain by following the steps below:
-
In the Group Policy Management Editor window, navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Audit Policy.
-
In the right pane, configure the following audit policies:
-
Audit account management policy – Right-click it, and then click Properties. Select Define these policy settings, select both the Success and Failure checkboxes. Click Apply then OK.
-
Audit directory service access – Right-click it, and then click Properties. Select Define these policy settings, select the Success checkbox. Click Apply then OK.
-
-
To apply the policy immediately, open an elevated Command Prompt and run the following command: gpupdate /force.
-
-
Enable the advanced audit policy in the source and destination domain by following the steps below:
-
In the Group Policy Management Editor window, navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > Account Management.
-
In the right pane, configure the following policies by right-clicking each one and selecting Properties. Then click Configure, select both the Success and Failure checkboxes, and click Apply and then OK.
-
Audit Application Group Management
-
Audit Computer Account Management
-
Audit Distribution Group Management
-
Audit Other Account Management Events
-
Audit Security Group Management
-
Audit User Account Management
-
-
In the Group Policy Management Editor window, navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies > DS Access.
-
In the right pane, configure the following policies by right-clicking each one and selecting Properties. Then click Configure, select the Success checkbox, and click Apply and then OK:
-
Audit Detailed Directory Service Replication
-
Audit Directory Service Access
-
Audit Directory Service Changes
-
Audit Directory Service Replication
-
-
To apply the policy immediately, open an elevated Command Prompt and run the following command: gpupdate /force.
NOTEIt may also be necessary to reboot the domain controller to have auditing take effect. Even with group policy applied on the default domain controller for the domain audit, the server audit setting on the primary domain controller (PDC) may not be enabled. Please confirm this setting is enabled for the local security policy on the PDC server. If not enabled, use the local security policy to enable this setting.
-
Account Permissions
To perform a SID History migration, specific permissions must be configured in both the source and target domains:
Uninstall the Agent
Refer the following steps to uninstall the agent:
-
Navigate to the Control Panel on the machine where you have installed agent, and click Uninstall a program.
-
Right-click the agent and select Uninstall/Change.
-
In the pop-up window, click OK.
-
Select the Delete the built-in database and configuration files checkbox if you want to delete the built-in database and configuration files generated by the agent installation.
If you want to retain the settings or job information, make sure the checkbox is not selected. Next time you install the agent, the data stored in the built-in database can be retrieved.
-
Click Uninstall to uninstall the agent.
Upgrade the Agent
Refer to the following steps to upgrade the agent:
-
Open the agent and click Learn more in the lower-left corner of the window. Then, the configurations window appears.
-
Click Check for a new version to check if there is an upgrade available for the agent. If no new version is detected, a message will be displayed next to the current version indicating that the Active Directory migration agent is up to date. If a new version is detected, the Upgrade now button will be displayed next to the current version. You can click it to upgrade the agent.
-
By default, the Auto check for a new version feature is enabled. A new version will be automatically detected at 0:00 every day on the machine where the agent is installed. You can also disable the Auto check for a new version feature to not auto detect the upgrades.
-
*Note: The auto upgrade will fail when the agent is running.
