Home > Perform Exchange Online Migrations > Required Permissions for Exchange Online Migration > Permissions for Destination Gmail
Export to PDFPermissions for Destination Gmail
To migrate to destination Gmail, the Super Admin can refer to to connect your Google tenant to AvePoint Online Services at first. Then, you need to create a custom Google app profile in AvePoint Online Services > Management > App management to connect to the Google tenant.
Refer to the following section for details about how to create a custom Google app profile with required permissions.
Create a Custom Google App Profile
To use a custom Google app profile, refer to the following steps and required permissions:
-
Click Create on the App management page in AvePoint Online Services.
-
In the Select services step, select a Google tenant, and choose Fly.
-
Click Next to go to the Choose setup methodstep.
-
In the Choose setup method step, select the Custom mode.
-
Click Next to go to the Consent to apps step.
-
In the Consent to apps step, enter the app profile name, admin account, Google service account, and private key of your app.
-
Click Finish.
Refer to the following sections about permissions required for the custom app.
API Requirements
Make sure the following APIs are enabled in the projects where the service accounts are created.
Refer to the following steps to enable the APIs:
The user must be the project owner to enable the APIs.
-
Go to .
-
Click ENABLE APIS AND SERVICES. The API library page appears.
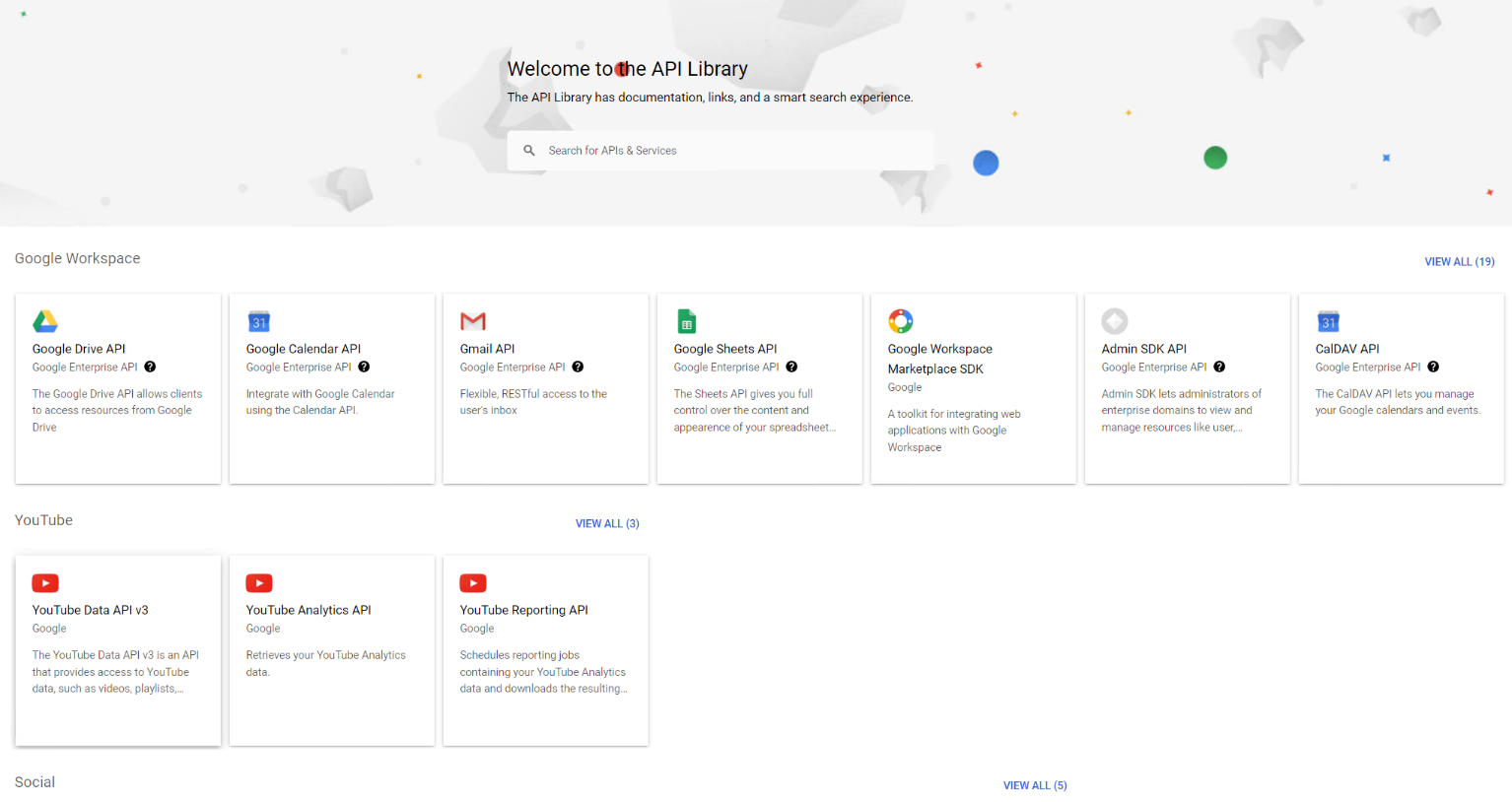
-
Click the API you want to enable respectively.
-
Click ENABLE on the top of the page to enable the corresponding API.
Make sure the API Access in your Google Workspace environment is enabled. Follow the provided by Google to ensure all your settings meet the requirements.
Admin Account Permissions
Make sure the Admin account has the following custom roles.
| Type | Admin Account Permission | Purpose |
|---|---|---|
| Gmail | Users > Read | Migrate Gmail mailboxes. |
| Gmail | Users > Update > Add/Remove Aliases | Migrate mailbox aliases |
| Gmail | Calendar > All Settings > Buildings and Resources > Room Insights | Migrate Gmail mailboxes. |
| Gmail | Groups > Update & Read | Get and add group members. |
| Gmail | Make changes to events permission to the calendar, or assign the Super Admin role to the Admin account. | Migrate private calendar events in the resource mailbox. |
The user must have the Super Admin role to assign permissions and manage roles.
To manage the roles of the Admin account, refer to the following steps:
-
Go to the Google .
-
Click Manage in the Users section.
-
Click the user you want to assign the roles. The user profile page appears.
-
Click the down arrow (
 ) button in the Admin roles and privileges section.
) button in the Admin roles and privileges section. -
If you need to assign the Super Admin role to the Admin account, search Super Admin in the search box, then switch on the Assigned state (
 ) button to assign the role.
) button to assign the role. -
Click SAVE.
-
Click the Edit (
 ) button in the upper-right corner of the Roles section.
) button in the upper-right corner of the Roles section.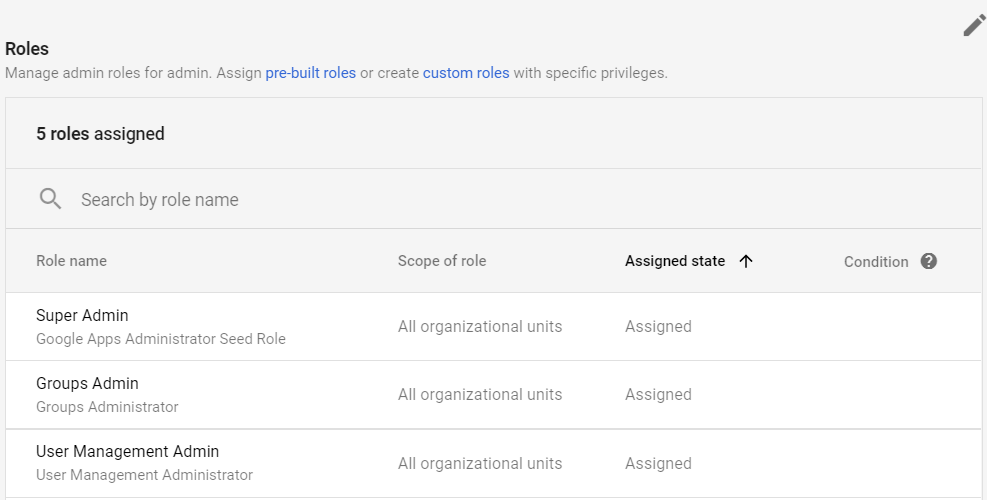
-
Click CREATE CUSTOM ROLE in the upper-right corner of the Roles section.
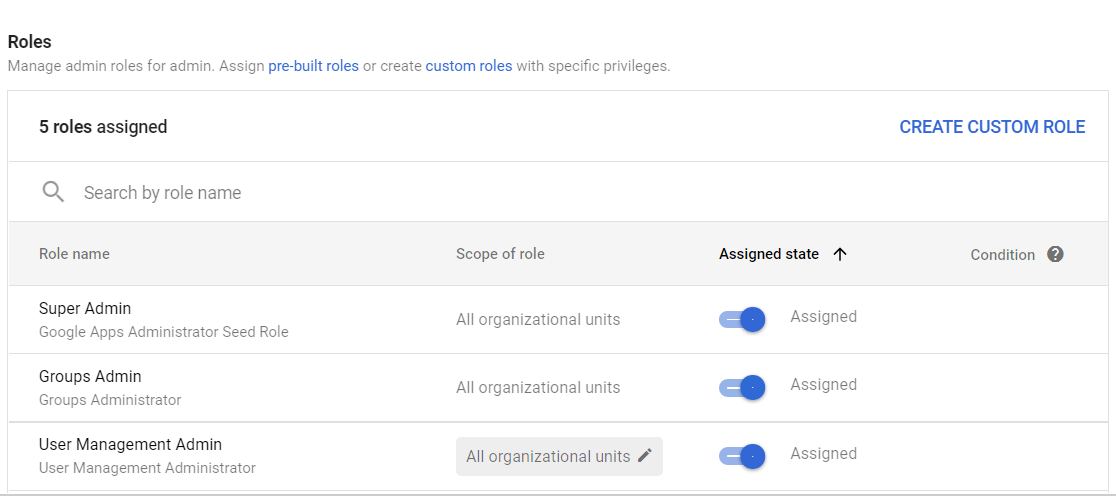
-
Click Create new role.
-
Enter a name for the current role and click CONTINUE.
-
In the Admin console privileges section, select the Room Insights privilege under the Calendar section; and if you want to perform the data discovery, also select the Reports privilege.
-
In the Admin API privileges section, select the Read privilege under the Users section and the Read privilege under the Groups section.
-
Click CONTINUE. The selected privileges will be listed on the Review Privileges page.
-
Click CREATE ROLE.
To assign the Make changes to events permission to the Admin account, refer to the following steps to subscribe and share the calendar to the Admin account:
-
Log in to Gmail using an account with the Super Admin role.
-
Click the Google apps (
 ) button and click the Calendar app.
) button and click the Calendar app. -
Click the add (
 ) button of the Other calendars at the bottom of the left pane, then click Browse resources.
) button of the Other calendars at the bottom of the left pane, then click Browse resources. -
Click the down arrow (
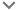 ) button of a resource and select the calendar you want to share with the Admin account. The selected calendar will be subscribed.
) button of a resource and select the calendar you want to share with the Admin account. The selected calendar will be subscribed. -
Click the desired calendar in the Settings for my calendars section in the left pane.
-
Click Add people under the Share with specific people section on the Settings page.
-
Add the Admin account you want to share the calendar in the first text box and select Make changes to events from the permissions drop-down list.
-
Click Send.
Google Service Account Permissions
To manage a Google service account, refer to the following steps:
The user must be the project owner to manage service accounts.
-
Go to the Google .
-
Select the desired project. The accounts in the projects are displayed.
-
To create a new service account, refer to the following steps:
NOTEIf you want to use an existing service account to add the Google Workspace connection, ignore this step.
-
Click CREATE SERVICE ACCOUNT.
-
Enter a service account name.
-
Enter the service account ID.
-
Enter the description for the service account.
-
Click CREATE AND CONTINUE. The service account is created.
-
Select the Owner role to the project from the drop-down list and click CONTINUE.
-
Click DONE.
-
-
A private key will be used when adding the connection. To obtain the private key of the service account, click the Actions (
 ) button of an existing service account, click Manage keys, click ADD KEY, and then select Create new key. Select the JSON type and click CREATE to download the private key file.NOTE
) button of an existing service account, click Manage keys, click ADD KEY, and then select Create new key. Select the JSON type and click CREATE to download the private key file.NOTEIf the service account key creation is disabled in your organization, enable it first by the following steps.
-
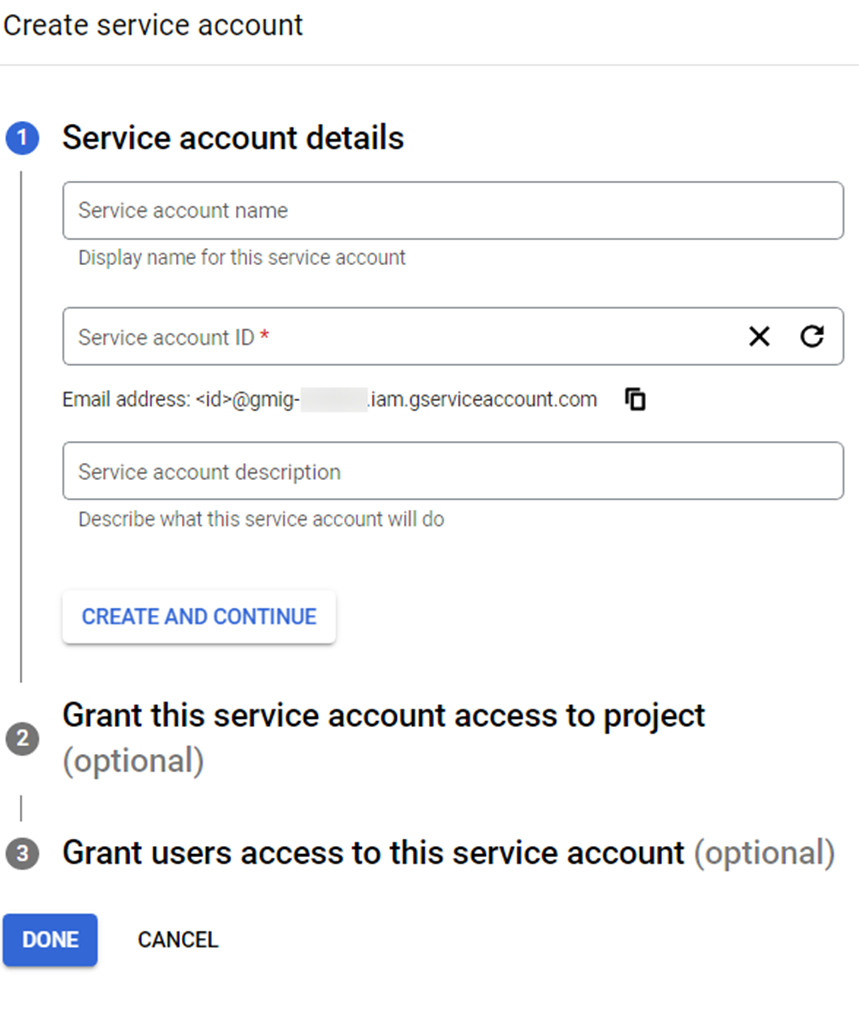
Navigate to Google Cloud > IAM & Admin > IAM.
-
Click the resource tab and click the domain name as the resource.
-
-
Click Grant access to access the Grant access to "[Tenant]" panel.
-
In the Add principals field, enter the email address of the signed-in user.
-
In the Assign roles field, select the Organization Policy Administrator role from the drop-down list.
-
Click Save to grant the role for the user to access the selected tenant.
-
Go to .
NOTEMake sure the current project is the project where you create the service account.
-
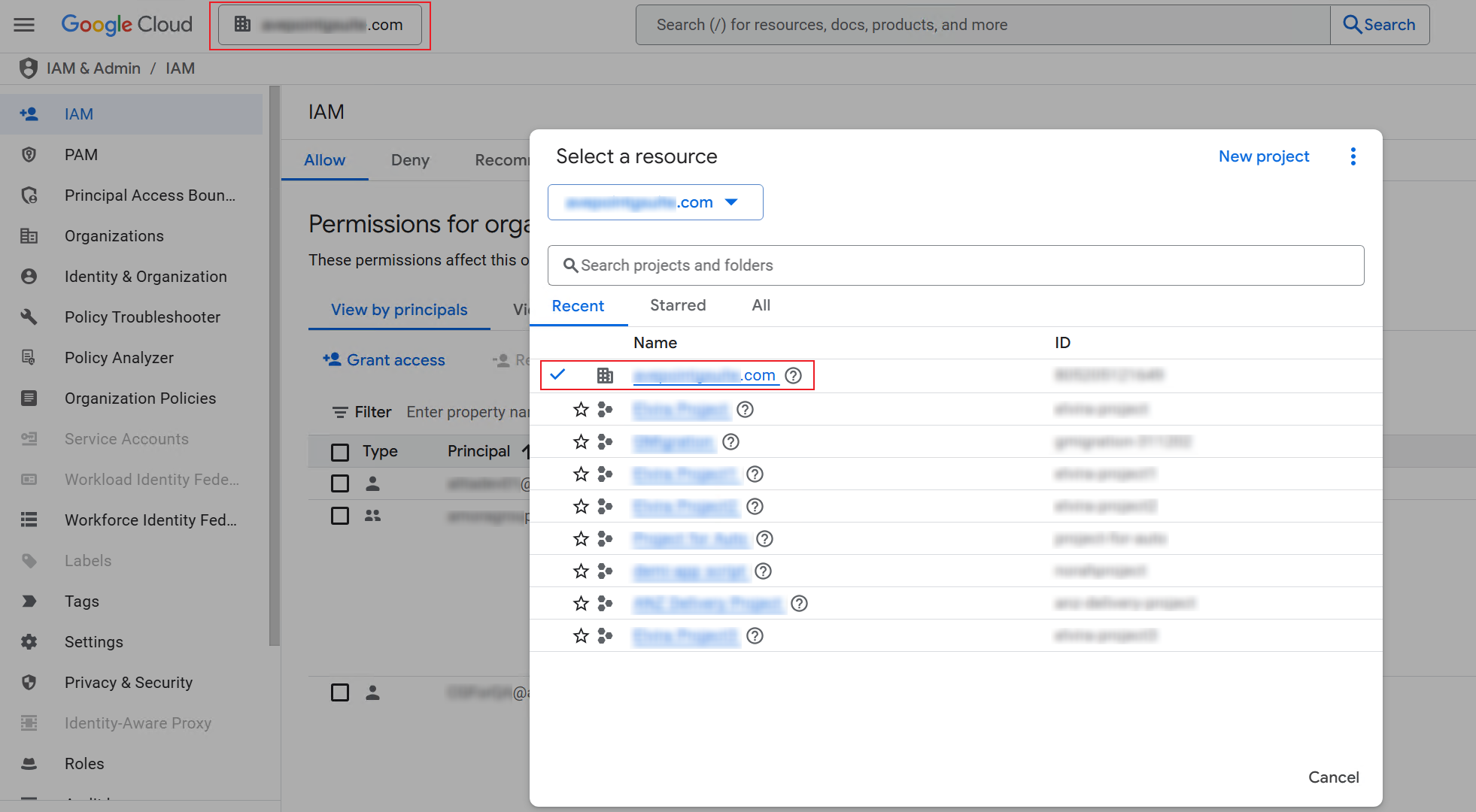
Click MANAGE POLICY.
-
Select Override parent's policy to set a unique policy for this project.
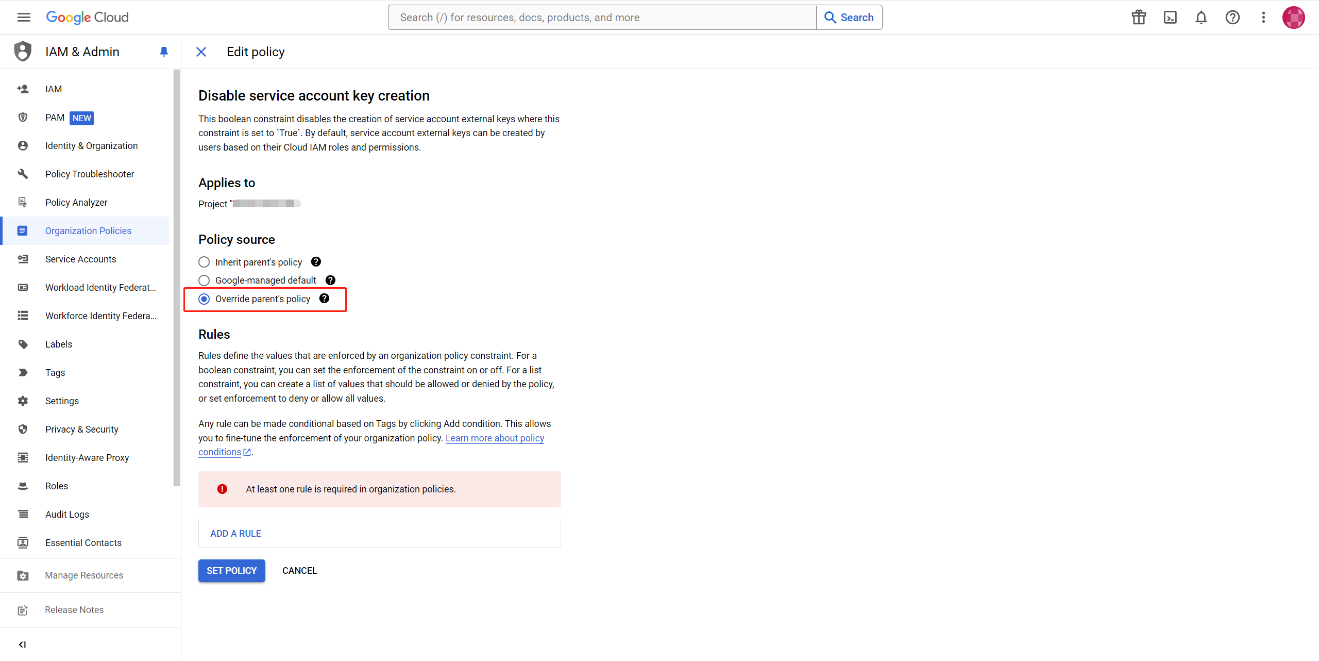
-
Click ADD A RULE to add a new rule.
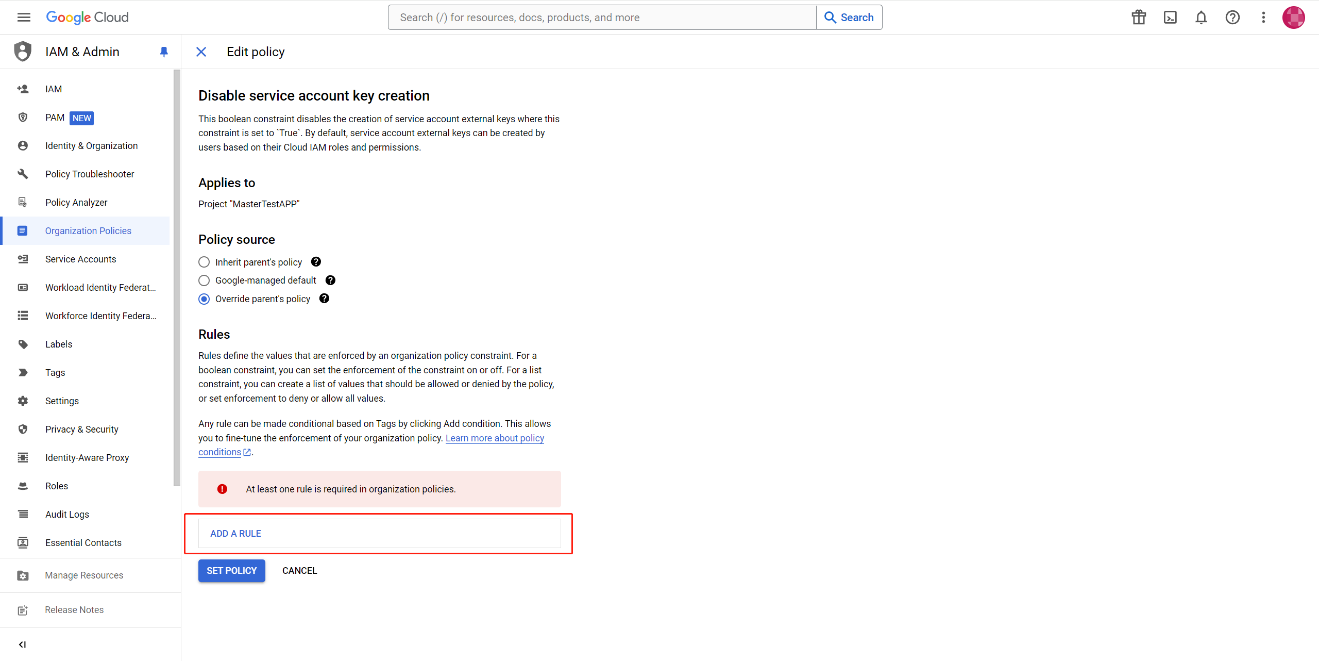
-
Select Off to disable the enforcement of the new rule, and click DONE.
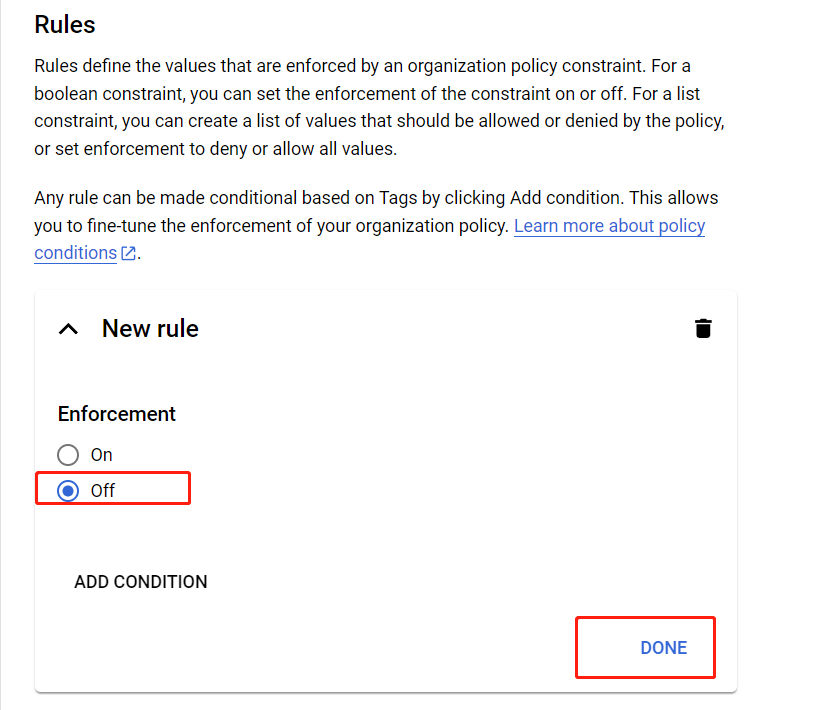
-
Click SET POLICY.
-
-
Open the .json file with Notepad and find the private key after the "private_key": node. The private key will be used when adding the connection.
-
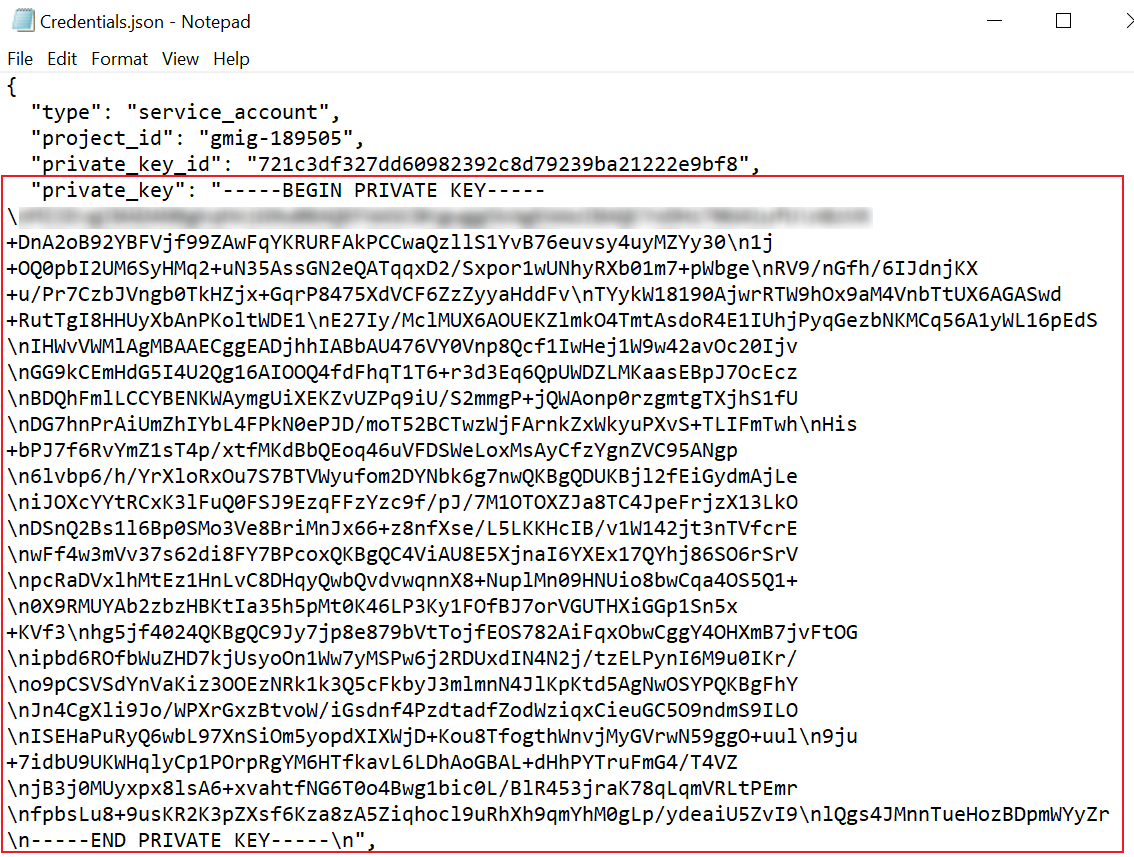
-
Go to the Google using the Super administrator credentials.
-
Navigate to Security > Overview > API controls.
-
Click MANAGE DOMAIN WIDE DELEGATION.
-
On the Domain-wide Delegation page, click Add new.
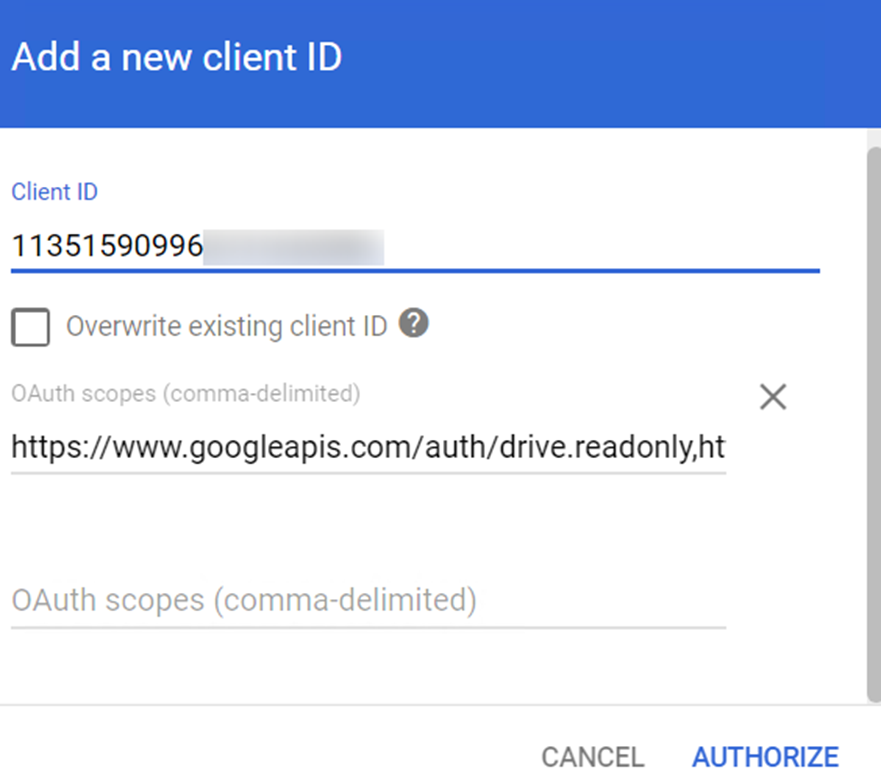
-
Enter the client ID of the service account in the Client ID field. The client ID can be found in the "client_id": " " node of the .json file in step 5.
-
Enter the following scopes in the OAuth scopes field:
The table below lists why the scopes are needed:
| Google Scopes Permission | Purpose |
|---|---|
| https://mail.google.com | Create mails and labels. |
| https://www.googleapis.com/auth/drive | Create folders, files, and permissions. |
| https://www.googleapis.com/auth/calendar | Create calendars and events. |
| https://www.googleapis.com/auth/admin.directory.user.readonly | List and get users in their domain for user mapping |
| https://www.googleapis.com/auth/admin.directory.group.readonly | List and get groups in their domain for user mapping |
| https://www.googleapis.com/auth/admin.directory.resource.calendar.readonly | Retrieve resource calendars. |
| https://www.googleapis.com/auth/admin.directory.group | Add group members |
| https://www.googleapis.com/auth/admin.directory.user.alias | Migrate mailbox aliases |
| https://www.googleapis.com/auth/apps.groups.migration | Migrate emails to Google group |
| https://www.googleapis.com/auth/contacts | Create contacts |
| https://www.googleapis.com/auth/tasks | Create tasks |
| https://www.googleapis.com/auth/gmail.settings.basic | Create filters |
- Click AUTHORIZE.
