Home > Get Started > Enable Backup for Microsoft Entra ID or Admin Portal Settings
Export to PDFEnable Backup for Microsoft Entra ID or Admin Portal Settings
To back up the Microsoft Entra ID or Admin Portal Settings, you can choose to create a service app, or use a custom Azure app with required permissions. For details on creating a custom Azure app, refer to . You can go to the Default Permissions Granted to the Service App section to find the permissions that you can grant to your custom app.
Complete the steps below:
-
Before you enable the backup service for Microsoft Entra ID or Admin Portal Settings, go to AvePoint Online Services to configure a service app profile for that Microsoft 365 tenant. For detailed instructions on creating a service app profile, refer to Create a Service App and Grant Consent.
-
After the service app is ready, go to the Backup page of the Cloud Backup for IaaS + PaaS to configure the backup scope for the Microsoft Entra ID or Admin Portal Settings. Note that if you have multiple tenants to protect, you must create a service app for each of them.
For details on configuring the backup scope, refer to:
Note the following:
-
If you want to back up and restore distribution lists or mail-enabled security groups in Microsoft Entra ID, or back up and restore the Microsoft 365 Defender or Exchange settings through Admin Portal Settings service, you can choose to configure a service account profile for this tenant with a Global Administrator or Exchange Administrator user role, or you can go to the Azure portal to add this service app as Exchange Administrators role. For details on assigning an app the Exchange administrator role, refer to . For details on configuring a service account profile, refer to .
-
A service account with MFA enabled is currently not supported. In addition, due to API limitations, the backup service of Microsoft Entra ID will perform full backups on the distribution lists and mail-enabled security groups each time. This can be determined by the number of successful objects in each backup job.
-
If you are using a custom Azure app for Microsoft Entra ID or Admin Portal Settings service and you do not want to assign a Global administrator or Exchange administrator role to the app, refer to the instructions in Create a Custom Role Group to create a role group with the minimum permissions. This configuration is only applicable to the custom app.
-
If you want to restore a temporarily deleted user or group, the service account or the service app must be assigned with the Global administrator role.
-
If you want to back up and restore the Self Service Group Management property of the Groups General settings for Microsoft Entra ID > Groups, you must configure a service account profile in the AvePoint Online Services interface with the service account in Cloud Application Administrator role. Note that if you only want to back up this property, the Cloud Application Administrator role is not required.
-
To back up and restore the Attributes and Claims, Identifier (Entity ID), currentSingleSignOnMode, ParentAppId, or IsCustomApp of the SSO configuration for the enterprise applications, you must have a service account profile configured in the AvePoint Online Services interface and the service account you use must have the Application Administrator role. Note that if you only want to back up this property, the Application Administrator role is not required.
For details on the support list, refer to Microsoft Entra ID and Admin Portal Settings.
Create a Service App and Grant Consent
To use Microsoft Entra ID's backup and restore services, create a service app to connect to your tenant and grant the requested permissions.
Creating an app profile requires a Microsoft 365 Global Administrator account to consent.
*Note: If you want to restore temporarily deleted users or groups, this service app must also be added as Global Administrator.
Follow the steps below to create the service app:
-
On the Management > App management page, click Create on the action bar.
-
In the Select services step, select Cloud Backup for IaaS + PaaS.
-
In the Choose setup method step, select Modern mode and click Next.
-
In the Consent to apps step, click Consent next to the Cloud Backup for Azure.
-
On the Microsoft 365 sign-in page, sign in with a Microsoft 365 Global Administrator account.
-
On the Permissions required page, review the permissions required and click Accept to continue. For the API permissions that this app requests, refer to Default Permissions Granted to the Service App.
-
The app profile you created will be displayed on the App management page, and the Cloud Backup for Azure app will be added to your Microsoft Entra admin center > enterprise applications.
Default Permissions Granted to the Service App
As of the December 2023 release, you can choose to use a custom Azure app with specific permissions for the data that you only want to protect*.*
All the API permissions required for Microsoft Entra ID and Admin Portal Settings services are listed in this table and they are automatically added to the service app after consent. For custom app permissions, you can choose to only add the corresponding permissions to protect the specific data types or add their alternative permissions (if available) for backup only purpose*.*
If you want to protect Microsoft Entra ID or the Admin Portal Settings, you can choose to create a Cloud Backup for Azure service app profile or create a custom Azure app profile with delegated permissions through AvePoint Online Services > Management > App management page. Note that if you do not use the Microsoft Entra ID backup service to protect the BitLocker recovery keys for the devices, you can choose to create any type of custom Azure app.
The following API permissions will be automatically added to the service app with consent from your Global administrator account. You can also choose the specific permissions to grant your custom Azure app for the services or data types that you want to protect upon the usage purpose.
*Note: If you remove the Global administrator role for the user after consenting, to ensure the protection of BitLocker keys, the consent user must be in one of the following roles: Cloud device administrator, Helpdesk administrator, Intune service administrator, Security administrator, Security reader, or Global reader. Otherwise, the user must be the registered owner of the device that the BitLocker recovery key was originally backed up from.
| API | Permissions | Type | Why You Need | Permission Category | Alternative Permission for backup only |
|---|---|---|---|---|---|
| Microsoft Graph | AdministrativeUnit.ReadWrite.All(Read and write administrative units.) | Application | Allows the app to create, read, update, and delete administrative units and manage administrative unit membership on behalf of the signed-in user. | Microsoft Entra ID > backup and restore of Administrative Units. | AdministrativeUnit.Read.All(Read all administrative units.) |
| Microsoft Graph | Application.ReadWrite.All(Read and write all apps.) | Application | Allows the app to create, read, update and delete applications and service principals on behalf of the signed-in user. | Microsoft Entra ID > backup and restore of applications. | Application.Read.All(Read all applications) |
| Microsoft Graph | AppRoleAssignment.ReadWrite.All(Manage app permission grants and app role assignments.) | Application | Allows the app to manage permission grants for application permissions to any API (including Microsoft Graph) and application assignments for any app, on behalf of the signed-in user. | Microsoft Entra ID > backup and restore of application role assignment. | |
| Microsoft Graph | AuditLog.Read.All(Read all audit log data.) | Application | Allows the app to read and query your audit log activities, without a signed-in user. | Microsoft Entra ID > backup of the Audit Logs and Sign-in Logs. | |
| Microsoft Graph | BitlockerKey.Read.All (Read all BitLocker keys) | Application | Allows an app to read BitLocker keys for all devices, without a signed-in user. Allows read of the recovery key. | Microsoft Entra ID > backup of Device BitLocker keys. | |
| Microsoft Graph | BitlockerKey.Read.All (Read all BitLocker keys) | Delegated | Allows an app to read BitLocker keys for all devices, without a signed-in user. Allows read of the recovery key. | Microsoft Entra ID > backup of Device BitLocker keys. | |
| Microsoft Graph | DeviceManagementApps.Read.All(Read Microsoft Intune apps.) | Application | Allows the app to read the properties, group assignments, and status of apps, app configurations, and app protection policies managed by Microsoft Intune. | Admin Portal Settings > backup of the app configuration policies in Microsoft Intune. | |
| Microsoft Graph | DeviceManagementApps.ReadWrite.All(Read and write Microsoft Intune apps.) | Application | Allows the app to read and write the properties, group assignments and status of apps, app configurations and app protection policies managed by Microsoft Intune, without a signed-in user. | Admin Portal Settings > restore of the supported Intune settings, such as apps properties, app configurations, and app protection policies. | |
| Microsoft Graph | *DeviceManagementApps.ReadWrite.All(Read and write Microsoft Intune apps.) | Delegated | Allows the app to read and write the properties, group assignments and status of apps, app configurations and app protection policies managed by Microsoft Intune, without a signed-in user. | Admin Portal Settings > restore of the supported Intune settings, such as apps properties, app configurations, and app protection policies. | DeviceManagementApps.Read.All |
| Microsoft Graph | DeviceManagementConfiguration.Read.All(Read Microsoft Intune device configuration and policies.) | Application | Allows the app to read properties of Microsoft Intune-managed device configuration and device compliance policies and their assignment to groups. | Admin Portal Settings > backup of device policies in Microsoft Intune. | |
| Microsoft Graph | DeviceManagementConfiguration.ReadWrite.All(Read and write all Microsoft Intune device configuration and policies.) | Application | Allows the app to read and write properties of Microsoft Intune-managed device configuration and device compliance policies and their assignment to groups, without a signed-in user. | Admin Portal Settings > restore of device policies in Microsoft Intune | |
| Microsoft Graph | DeviceManagementRBAC.Read.All(Read Microsoft Intune RBAC settings) | Application | Allows the app to read the properties relating to the Microsoft Intune Role-Based Access Control (RBAC) settings, without a signed-in user. | Admin Portal Settings > backup of the supported Intune settings, such as policy properties. | |
| Microsoft Graph | DeviceManagementScripts.ReadWrite.All(Read and write Microsoft Intune Scripts) | Application | Allows the app to read and write Microsoft Intune device compliance scripts, device management scripts, device shell scripts, device custom attribute shell scripts and device health scripts, without a signed-in user. | Admin Portal Settings > backup and restore of Intune Devices Scripts settings. | DeviceManagementScripts.Read.All(Allows the app to read Microsoft Intune device compliance scripts, device management scripts, device shell scripts, device custom attribute shell scripts and device health scripts, without a signed-in user.) |
| Microsoft Graph | Directory.ReadWrite.All(Read and write directory data.) | Application | Allows the app to read and write data in your organization's directory, such as users, and groups. It does not allow the app to delete users or groups, or reset user passwords. | Microsoft Entra ID > backup and restore of users and groups. | Directory.Read.All(Read directory data.) |
| Microsoft Graph | Domain.Read.All(Read domains) | Application | Allows the app to read all domain properties without a signed-in user. | Microsoft Entra ID > restore users. | |
| Microsoft Graph | Group.ReadWrite.All(Read and write all groups.) | Application | Allows the app to create groups and read all group properties and memberships on behalf of the signed-in user. Also allows the app to read and write calendars, conversations, files, and other group content for all groups the signed-in user can access. Additionally allows group owners to manage their groups and allows group members to update group content. | Microsoft Entra ID > backup and restore of groups. | Group.Read.All(Read all groups.) |
| Microsoft Graph | Organization.Read.All(Read organization information) | Application | Retrieves all the organizational brandings. | Admin Portal Settings > backup of Company Branding Settings. | |
| Microsoft Graph | Policy.Read.All(Read your organization's policies) | Application | Allows the app to read all your organization's policies without a signed in user. | Microsoft Entra ID > restore users to another tenant.Admin Portal Settings > backup of Conditional Access and Named Locations. | |
| Microsoft Graph | Policy.ReadWrite.ApplicationConfiguration(Read and write your organization’s application configuration policies.) | Application | Allows the app to read and write your organization’s application configuration policies on behalf of the signed-in user. | Microsoft Entra ID > backup and restore for the SSO configurations of Enterprise applications. | |
| Microsoft Graph | Policy.ReadWrite.AuthenticationMethod(Read and write all authentication method policies) | Application | Retrieves all the authentication method policies and configurations. | Admin Portal Settings > backup of Authentication Methods. | |
| Microsoft Graph | Policy.ReadWrite.Authorization(Read and write your organization’s authorization policy.) | Application | Allows the app to update the group general settings to enable or disable the capability for users to create security groups. | Admin Portal Settings > backup and restore of the group general settings. | |
| Microsoft Graph | Policy.ReadWrite.ConditionalAccess(Read and write your organization's conditional access policies.) | Application | Allows the app to read and write your organization's conditional access policies, without a signed-in user. | Admin Portal Settings > backup and restore of the conditional access. | Policy.Read.ConditionalAccess(Read your organization's conditional access policies) |
| Microsoft Graph | RoleManagement.ReadWrite.Directory(Read and write all directory RBAC settings.) | Application | Allows the app to read and manage the role-based access control (RBAC) settings for your company's directory, on behalf of the signed-in user. This includes instantiating directory roles and managing directory role membership, and reading directory role templates, directory roles and memberships. | Microsoft Entra ID > backup and restore of roles and administrators. | |
| Microsoft Graph | User.Read(Sign in and read user profile.) | Delegated | Allows users to sign into AvePoint Online Services with Microsoft 365 accounts. | Sign into AvePoint Online Services with Microsoft 365 accounts. | |
| Microsoft Graph | User.ReadWrite.All(Read and write all users’ full profiles.) | Application | Allows the app to read and write the full set of profile properties, reports, and managers of other users in your organization, on behalf of the signed-in user. Also allows the app to create and delete users as well as reset user passwords on behalf of the signed-in user. | Microsoft Entra ID > backup and restore of users. | User.Read.All(Read all users' full profiles) |
| Microsoft Graph | UserAuthenticationMethod.ReadWrite.All(Read and write all users' authentication methods) | Application | Allows the application to read and write authentication methods of all users in your organization without a signed-in user. Authentication methods include information like a user’s phone number and Authenticator app settings. This does not allow the app to see sensitive information, such as the password, or to sign in or use the authentication methods. | Microsoft Entra ID > backup and restore of User Authentication Methods. | UserAuthenticationMethod.Read.All(Read all users’ authentication methods.) |
| Office 365 Exchange Online | Exchange.ManageAsApp(Manage Exchange as application) | Application | Allows the backup and restore of the distribution lists. | Microsoft Entra ID > backup and restore of distribution lists.Admin Portal Settings > backup and restore of Exchange and Defender settings. |
Create a Custom Role Group
If you want to protect distribution lists or mail-enabled security groups in Microsoft Entra tenant through the Microsoft Entra ID service, or to protect Microsoft 365 Defender or Exchange admin center settings through the Admin Portal Settings service, you can choose to assign the Exchange administrator role to the app that you created for Microsoft Entra ID and Admin Portal Settings services. If you are using a custom app and you do not want to assign the Exchange administrator role to the app in this case, you can now create a role group through Exchange admin center with minimum permissions and add the app as the group member.
Note that this configuration is only applicable to the custom app.
Follow the steps below:
-
Sign in to the Exchange admin center with an administrator account.
-
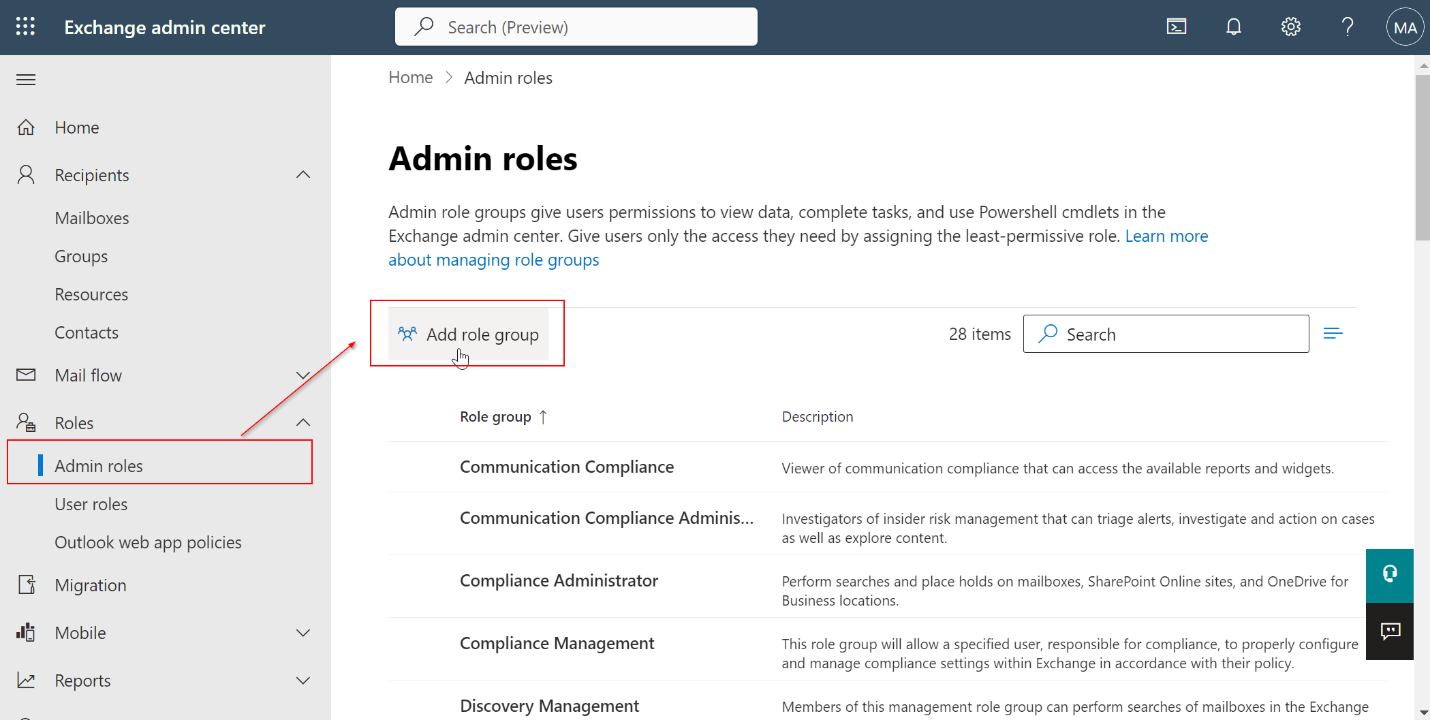
Navigate to Roles > Admin roles.
-
Click Add role group.
-
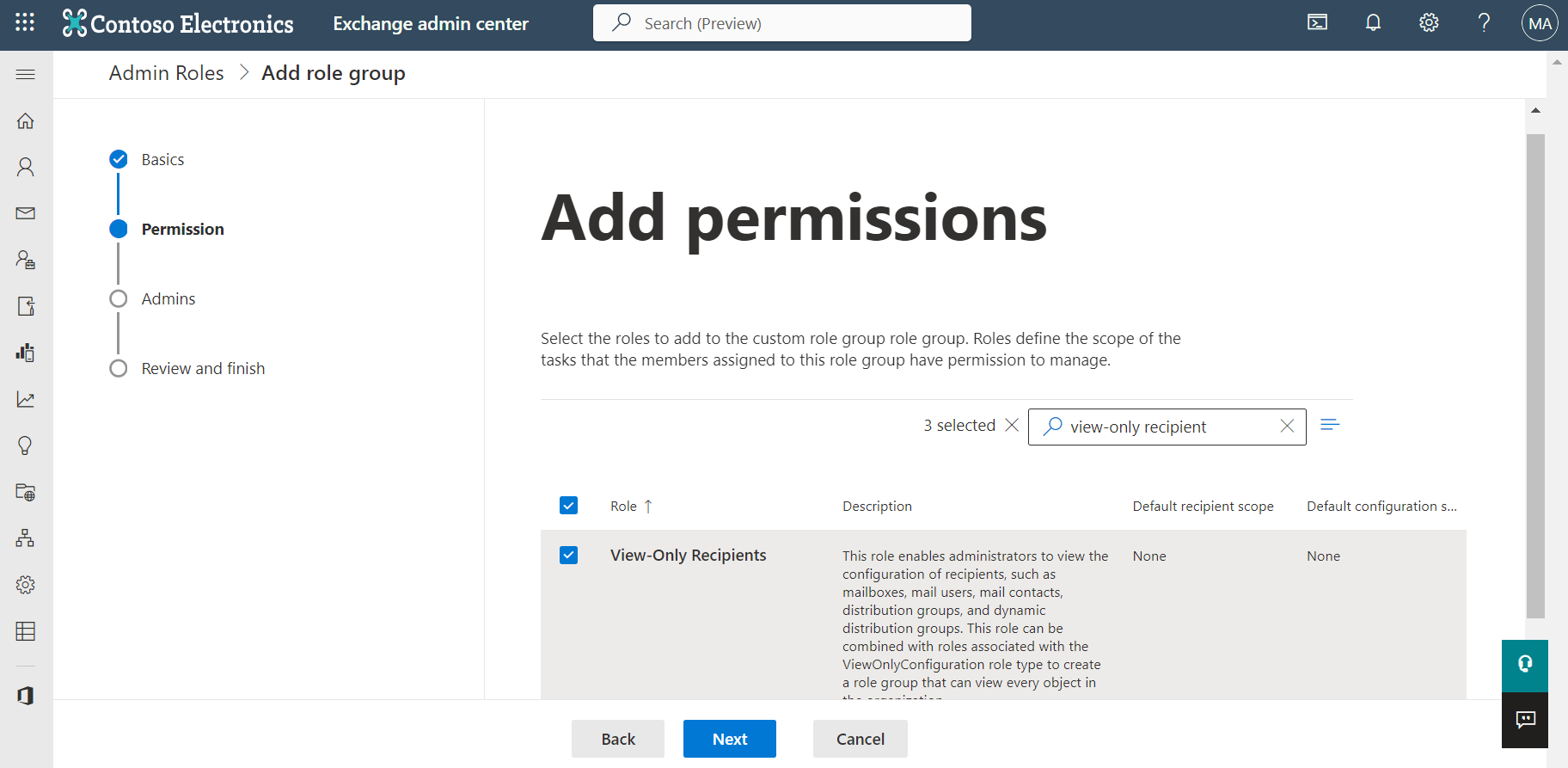
Provide the basic information for the role group and go to the Permission step.
-
In the Add permissions page, select the following permissions:
-
Mail Recipients
-
View-Only Configuration
-
View-Only Recipients
-
-
Click Next, continue to complete the other settings, and click Add role group to finish.
-
After the role group with the required permissions has been added, follow the steps below to add the app to the role group as a group member:
-
Run PowerShell as an administrator on your computer.
-
Install Exchange Online via PowerShell using the following command lines:
Install-Module -Name ExchangeOnlineManagement -RequiredVersion 3.4.0
Set-ExecutionPolicy RemoteSigned
-
Execute the following command lines to add the app as a member of the role group that you have created
*Note: You must provide the Application ID, Object ID, and the Display Name of the app. You can go to the Azure portal > Enterprise applications page for the app information.
Connect-ExchangeOnline
New-ServicePrincipal -AppId -ObjectId -DisplayName
Add-RoleGroupMember "" -Member
-
