Home > About AvePoint Cloud Backup for IaaS + PaaS
Export to PDFAbout AvePoint Cloud Backup for IaaS + PaaS
AvePoint Cloud Backup ensures the resiliency of service in the event of a disaster and quickly recovers lost or corrupted content from your backup.
AvePoint Cloud Backup for IaaS + PaaS (formerly, Cloud Backup for Azure) offers data recovery capabilities for your Virtual Machines (Azure VMs, Amazon EC2 instances, and Google VM instances), Microsoft Entra ID, Azure Storage (blob storage and file share), Admin Portal Settings, Azure SQL (for Azure SQL databases), Azure DevOps, Azure AD B2C, and AWS Platform Configurations (Private preview).
The new redesigned user interface, available since the February 2024 release, is now the primary UI of the solution.
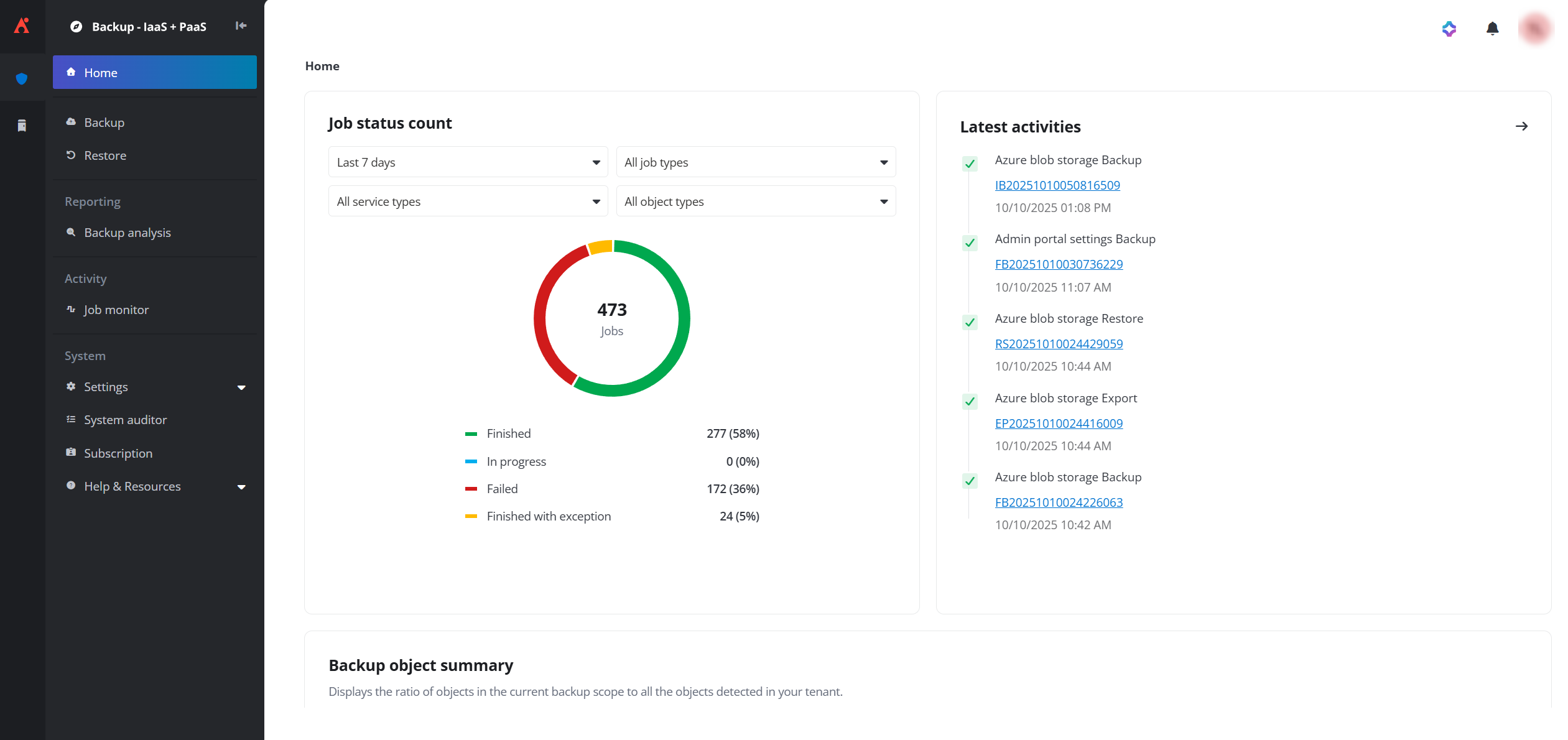
The new Home page UI.
AvePoint Cloud Backup for IaaS + PaaS is now only available in the following data centers: Australia Southeast (Victoria), Canada Central (Toronto), Germany West Central (Frankfurt), West Europe (Netherlands), UK South (London), North Europe (Ireland), Japan West (Osaka), East US (Virginia), Southeast Asia (Singapore), Switzerland North (Zurich), France Central (Paris), Korea Central (Seoul), US Gov Virginia (Virginia), and United Arab Emirates (Dubai).
In addition, if your browser’s first preferred language is Japanese, French, or German, the Cloud Backup for IaaS + PaaS interface will be displayed in Japanese, French, or German. In other cases, the interface will be displayed in English.
*Note: To access the user guide, expand the Help & Resources section on the left navigation and click User guide. If you encounter any issues when using AvePoint Cloud Backup for IaaS + PaaS services, you can expand the Help & Resources section and click Invite support to go to the AvePoint Online Services interface to submit an issue to AvePoint support for assistance.
The dashboard on the home page provides a comprehensive overview of the latest activities, job status count, backup object summary, restore job summary, storage space usage, and the storage profile usage rank.
The Backup page shows the Microsoft Entra ID tile, the Virtual Machine tile, the Azure Storage tile, the Admin Portal Settings tile, the Azure SQL tile, the Azure DevOps tile, the Azure AD B2C tile, and the AWS Platform Configurations (Private preview) tile.
Through each service tile, you can view the backup and restore details of its latest jobs, including backup scope name, job duration, operator, latest restore history, etc. Additionally, you can update the backup scopes and frequency.
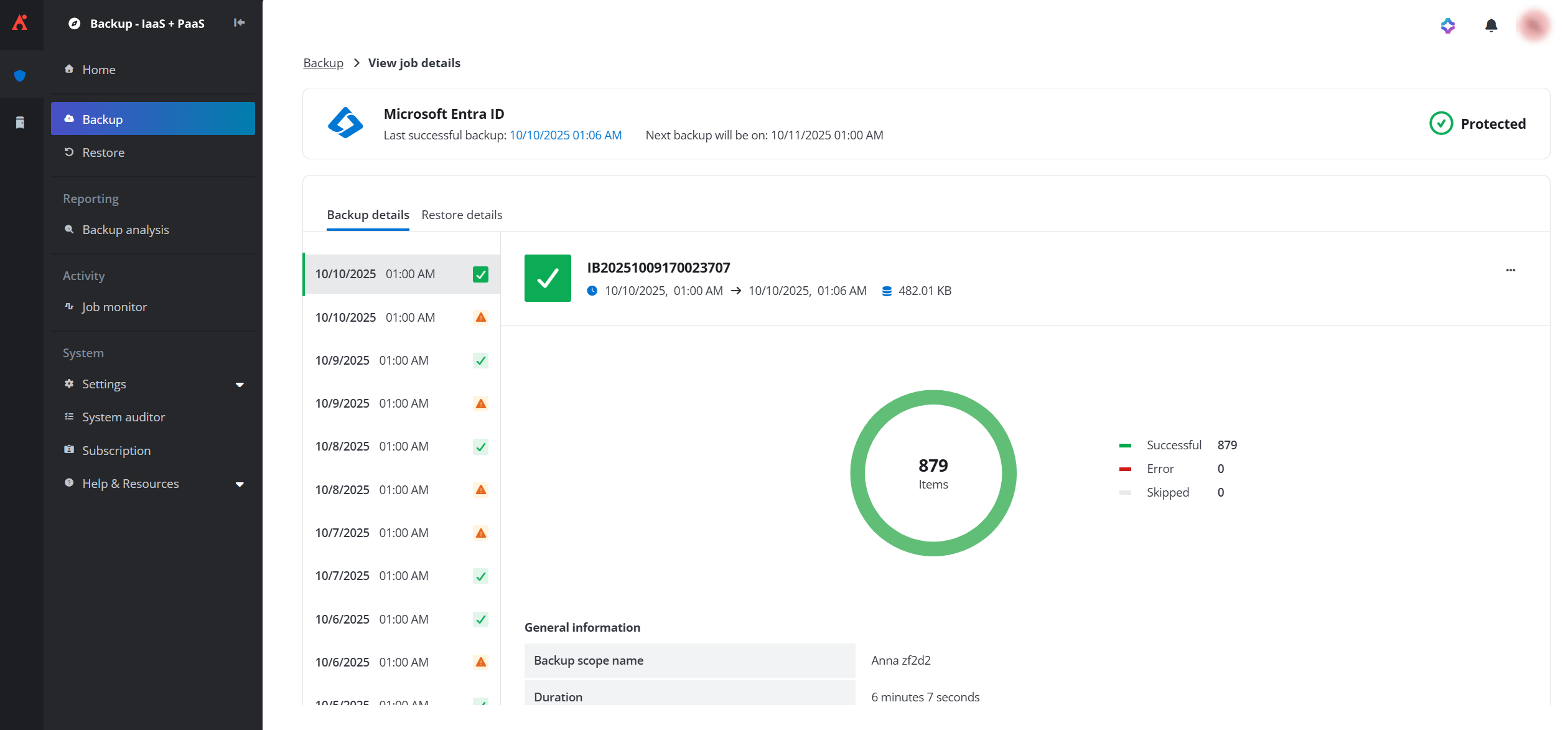
View backup and restore details on the new UI (through Backup > View job history).
If you are in trial, your experience with the backup services in Cloud Backup for IaaS + PaaS will be limited:
*Note: If you want to have an unlimited trial experience, you can contact AvePoint support for help.
Enable Backup
To use Cloud Backup for IaaS + PaaS to protect Microsoft Entra ID, Azure VMs, Azure Storage, Admin Portal Settings, Azure SQL, Amazon EC2 instances, Azure DevOps, Azure AD B2C, or AWS Platform Configurations (Private preview), you must connect your Microsoft or Amazon tenant to AvePoint Online Services. For details, refer to .
Note the following before you enable the backup:
Single Sign-On
With Single Sign-On(SSO) supported, you can access Cloud Backup for IaaS + PaaS interface via direct URL without providing user credentials, once it is detected that you have signed into the AvePoint Online Services interface.
Beta APIs
Refer to the table below for the beta version API methods of Microsoft Graph that we use in AvePoint Cloud Backup for IaaS + PaaS.
| Category | API Method | Is it available in the 1.0 version? | Then, why do we use the Beta version? |
|---|---|---|---|
| Microsoft Entra ID > groups | Groups resource type | No | Write back group configurations |
| Microsoft Entra ID > EnterpriseApplication | Synchronization API | No | For the backup and restore of the Enterprise Applications > Provisioning. |
| Microsoft Entra ID > EnterpriseApplication | Delete synchronizationJob | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Microsoft Entra ID > EnterpriseApplication | Create synchronizationJob | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Microsoft Entra ID > EnterpriseApplication | Update synchronizationSchema | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Microsoft Entra ID > EnterpriseApplication | synchronizationJob: pause | start | Yes |
| Microsoft Entra ID > EnterpriseApplication | Add synchronization secrets | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Microsoft Entra ID > EnterpriseApplication | Create unifiedRoleAssignment | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Microsoft Entra ID > EnterpriseApplication | GetAppDefaultClaim(Internal) | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Microsoft Entra ID > EnterpriseApplication | UpdateAppDefaultClaims(Internal) | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Microsoft Entra ID > SignInLogs | List signIns | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Microsoft Entra ID > Administrative Unit | Update administrativeUnit | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Admin Portal Settings | Get authenticationMethodsPolicy | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Admin Portal Settings | List policies | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Admin Portal Settings | List deviceCompliancePolicies | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Admin Portal Settings | *Get /deviceManagement/*compliancePolicies | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Admin Portal Settings | List deviceConfigurations | No | |
| Admin Portal Settings | *GET /deviceManagement/configurationPolicies?$*filter=technologies ne 'mdm,microsoftSense' | No | |
| Admin Portal Settings | *GET /deviceManagement/configurationPolicies?$*filter=technologies eq 'mdm,microsoftSense' | No | |
| Admin Portal Settings | Get deviceConfigurationAssignment | No | |
| Admin Portal Settings | List deviceManagementConfigurationPolicyAssignments | No | |
| Admin Portal Settings | List deviceManagementConfigurationSetting | No | |
| Admin Portal Settings | List groupPolicyConfigurations | No | |
| Admin Portal Settings | Get groupPolicyDefinitionValue | No | |
| Admin Portal Settings | List deviceManagementScripts | No | |
| Admin Portal Settings | List deviceShellScripts | No | |
| Admin Portal Settings | Get deviceManagementScriptRunSummary | No | |
| Admin Portal Settings | Get deviceManagementScriptDeviceState | No | |
| Admin Portal Settings | List deviceManagementScriptUserStates | No | |
| Admin Portal Settings | List managedAppPolicies | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Admin Portal Settings | Get androidManagedAppProtection | No | |
| Admin Portal Settings | Get iosManagedAppProtection | No | |
| Admin Portal Settings | Get mdmWindowsInformationProtectionPolicy | No | |
| Admin Portal Settings | Get windowsManagedAppProtection | No | |
| Admin Portal Settings | List managedDeviceMobileAppConfigurations | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Admin Portal Settings | Get managedDeviceMobileAppConfiguration | No | |
| Admin Portal Settings | Get managedDeviceMobileAppConfigurationAssignment | No | |
| Admin Portal Settings | List targetedManagedAppConfigurations | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Admin Portal Settings | *GET /deviceManagement/**intents?$**filter=*templateId ne 'e44c2ca3-2f9a-400a-a113-6cc88efd773d' | No | |
| Admin Portal Settings | *GET /deviceManagement/**intents?$**filter=*templateId eq 'e44c2ca3-2f9a-400a-a113-6cc88efd773d' | No | |
| Admin Portal Settings | Get targetedManagedAppConfiguration | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Admin Portal Settings | conditionalAccessPolicy resource type | Yes | Currently, there are some missing properties when using the Graph v1.0 endpoint. |
| Admin Portal Settings | List targetedManagedAppPolicyAssignments | No | |
| Admin Portal Settings | List deviceManagementIntents | No | |
| Admin Portal Settings | List deviceManagementIntegerSettingInstances | No | |
| Admin Portal Settings | Get deviceManagementTemplate | No | |
| Admin Portal Settings | Get deviceManagementIntent | No | |
| Admin Portal Settings | Get deviceManagementIntentDeviceStateSummary | No | |
| Admin Portal Settings | Get deviceManagementIntentUserStateSummary | No | |
| Admin Portal Settings | Get deviceManagementIntentUserState | No | |
| Admin Portal Settings | List deviceManagementIntentDeviceStates | No | |
| Admin Portal Settings | List deviceManagementIntentDeviceSettingStateSummaries | No | |
| Admin Portal Settings | Create conditionalAccessPolicy | Yes | Currently, there are some missing properties when using the Microsoft Graph v1.0 endpoint. |
| Admin Portal Settings | Update conditionalAccessPolicy | Yes | Currently, there are some missing properties when using the Microsoft Graph v1.0 endpoint. |
| Admin Portal Settings | Create defaultDeviceCompliancePolicy | No | |
| Admin Portal Settings | assign action | No | |
| Admin Portal Settings | Update windows10CompliancePolicy | No | |
| Admin Portal Settings | scheduleActionsForRules action | No | |
| Admin Portal Settings | Create deviceManagementCompliancePolicy | No | |
| Admin Portal Settings | setScheduledActions action | No | |
| Admin Portal Settings | Create conditionalAccessPolicy | Yes | |
| Admin Portal Settings | Update conditionalaccesspolicy | No | |
| Admin Portal Settings | Create windows10CustomConfiguration | No | |
| Admin Portal Settings | Create deviceManagementScript | No | |
| Admin Portal Settings | Update deviceManagementScript | No | |
| Admin Portal Settings | Create deviceManagementScriptAssignment | No | |
| Admin Portal Settings | Update deviceManagementScriptAssignment | No | |
| Admin Portal Settings | Create deviceManagementConfigurationPolicy | No | |
| Admin Portal Settings | Update deviceManagementConfigurationPolicy | No | |
| Admin Portal Settings | Create androidManagedAppProtection | No | |
| Admin Portal Settings | Create iosManagedAppProtection | No | |
| Admin Portal Settings | Create windowsManagedAppProtection | No | |
| Admin Portal Settings | Create mdmWindowsInformationProtectionPolicy | No | |
| Admin Portal Settings | Update androidManagedAppProtection | No | |
| Admin Portal Settings | Update iosManagedAppProtection | No | |
| Admin Portal Settings | Update windowsManagedAppProtection | No | |
| Admin Portal Settings | Update mdmWindowsInformationProtectionPolicy | No | |
| Admin Portal Settings | Create iosMobileAppConfiguration | No | |
| Admin Portal Settings | Update iosMobileAppConfiguration | No | |
| Admin Portal Settings | createInstance action | No | |
| Admin Portal Settings | Update deviceManagementIntent | No | |
| Admin Portal Settings | updateSettings action | No | |
| Admin Portal Settings | Create deviceManagementConfigurationPolicy | No | |
| Admin Portal Settings | Update deviceManagementConfigurationPolicy | No | |
| Admin Portal Settings | list hardwareconfigurations | No | |
| Admin Portal Settings | get hardwareconfigurations | No | |
| Admin Portal Settings | create hardwareconfigurations | No | |
| Admin Portal Settings | update hardwareconfigurations | No | |
| Admin Portal Settings | Get Presentation of Definition | No | |
| Admin Portal Settings | Get Presentation Value | No | |
| Azure AD B2C > User Flow | List Userflow | No | For the backup and restore of user flows. |
| Azure AD B2C > User Flow | Get Userflow | No | For the backup and restore of user flows. |
| Azure AD B2C > User Flow | Create Userflow | No | For the backup and restore of user flows. |
| Azure AD B2C > User Flow | Update Userflow | No | For the backup and restore of user flows. |
| Azure AD B2C > User Flow | Delete UserFlow | No | For the backup and restore of user flows. |
| Azure AD B2C > User Flow | List Identity provider | No | For the backup and restore of user flows. |
| Azure AD B2C > User Flow | Add Identity provider | No | For the backup and restore of user flows. |
| Azure AD B2C > User Flow | Delete Identity provider | No | For the backup and restore of user flows. |
| Azure AD B2C > User Flow | List user attribute assignment | No | For the backup and restore of user flows. |
| Azure AD B2C > User Flow | Create user attribute assignment | No | For the backup and restore of user flows. |
| Azure AD B2C > User Flow | Delete user attribute assignment | No | For the backup and restore of user flows. |
Backup Scope
When configuring the backup scope for virtual machines, Azure Storage, Azure SQL, or Admin Portal Settings, you can click the Refresh List button to retrieve the latest data information and keep your backup scope updated. It may take a long time. The product also provides a timer job to regularly refresh your data list at 0:00 AM every day, in your local time. The last refreshed time will be displayed next to the button.
*Note: If it is your first time using a service, you can click the Refresh List button to manually initialize the data list that can be added to the backup scope according to your settings.
The backup service for Azure VMs, Azure Storage, and Azure Admin Settings supports you – by grouping the backup of Azure VMs, Blob Storage, File Share, or admin portal settings into separate backup scopes. This will protect them with individual backup schedules or data retention settings. Note that the data in the Azure storage archive tier cannot be protected as the Cloud Backup for IaaS + PaaS cannot read or download a blob in the Archive tier. You must manually rehydrate the archive data that you want to protect to the online tier (cold, cool, or hot tier).
Each backup scope for Microsoft Entra ID can only protect one tenant. In addition, once you have created a backup scope, you cannot add the same tenant to another scope.
The backup services will perform scheduled backups automatically according to the settings of each backup scope. Note that if a backup job for the same backup scope is in progress, the automatic backup job scheduled to run will be skipped.
Storage Location
You can choose to use the default storage hosted by AvePoint to store your backup data or choose to use your own storage. Currently, you can choose from the following supported storage types for AvePoint-hosted default storage or for BYOS (bring your own storage).
| AvePoint Default Storage Type | BYOS Storage Type |
|---|---|
| Microsoft Azure Blob StorageAmazon S3 storageGoogle Cloud Storage*Note: The AvePoint-hosted Amazon S3 storage is only available in the commercial environment. | Microsoft Azure Blob StorageAmazon S3 storageAmazon S3-Compatible storageIBM Storage Protect – S3IBM Cloud Object StorageGoogle Cloud Storage |
*Note: The supported Azure storage account kinds are Storage and StorageV2 of Standard performance type. Note that the Azure Blob storage that has enabled Data Lake Storage Gen2 capabilities (a hierarchical namespace) is not supported.
For details on how to change from AvePoint default storage to BYOS storage and manage your storage profiles, refer to Manage Your Storage.
If you are using your own Microsoft Azure storage and backup retention period is longer than 45 days, your backup data will be automatically stored to the Cold tier for cost savings after the December 2023 release. For existing customers, your former backup data are still stored in the cool tier. To use your Azure blob storage in the most cost-effective manner, you can store your backup data to archive tier. However, Cloud Backup for IaaS + PaaS currently does not support restoring the backup data from the archive tier automatically. If you want to restore the backup data from the archive tier, you must rehydrate the data first. For details on Azure storage access tiers, refer to the Microsoft article: .
If you use your own Azure storage, AvePoint recommends using the Azure storage account from the same region as the object you want to back up, otherwise, the backup will incur data transfer costs. Data transfer costs are also incurred if you use AvePoint default storage and the Azure VMs or storage that is not in the same region as the AOS tenant that you’ve signed up for. See the information in this for bandwidth pricing that may be incurred due to the data transferred out of Azure data centers.
If you use AvePoint-hosted default storage, Availability Paired Region is now available as an option to replicate your data. To use availability paired region, go to the Cloud Operation Portal and configure your Cloud Backup for IaaS + PaaS settings by enabling the Availability Paired Region option.
Note the following:
If you use the AvePoint-hosted Amazon S3 storage, refer to the following data center mappings between the data center you signed up to AOS with, the data center of the Amazon S3 storage, and the paired secondary region.
If you enable the Availability Paired Region, it will be implemented through the Amazon Cross-Region Replication functionality. For more details, refer to this .
| Data Center You Signed Up for AOS(Home Region) | Amazon S3 Storage Data Center(Storage Region) | Availability Paired Region |
|---|---|---|
| East US (Virginia) | US East (N. Virginia) | US East (Ohio) |
| North Europe (Ireland) | Europe (Ireland) | Europe (Stockholm) |
| Southeast Asia (Singapore) | Asia Pacific (Singapore) | Asia Pacific (Jakarta) |
| Australia Southeast (Victoria) | Asia Pacific (Sydney) | Asia Pacific (Melbourne) |
| Japan West (Osaka) | Asia Pacific (Tokyo) | Asia Pacific (Osaka) |
| UK South (London) | Europe (London) | Europe (Milan) |
| Canada Central (Toronto) | Canada (Central) | Canada West (Calgary) |
| Germany West Central (Frankfurt) | Europe (Frankfurt) | Europe (Milan) |
| Korea Central (Seoul) | Asia Pacific (Seoul) | Asia Pacific (Tokyo) |
| France Central (Paris) | Europe (Paris) | Europe (Spain) |
| Switzerland North (Zurich) | Europe (Zurich) | Europe (Spain) |
| West Europe (Netherlands) | Not Supported | Not Supported |
| United Arab Emirates (Dubai) | Middle East (UAE) | Middle East (Bahrain) |
If you use the AvePoint-hosted Google Cloud storage, refer to the following data center mappings between the data center you signed up to AOS with, the data center of the Google Cloud Storage, and the paired secondary region.
If you enable the Availability Paired Region, it will be implemented through the Google Multi-region configuration. For more details, refer to this .
| Data Center You Signed Up for AOS(Home Region) | Google Cloud Storage Data Center(Storage Region) | Availability Paired Region |
|---|---|---|
| Australia Southeast (Victoria) | Sydney (australia-southeast1) | ASIA |
| Canada central (Toronto) | Canada Toronto (northamerica-northeast2) | US |
| Germany West Central (Frankfurt) | Germany Frankfurt (europe-west3) | EU |
| West Europe (Netherlands) | Netherlands (europe.west4) | EU |
| UK South (London) | United Kingdom London (europe-west2} | EU |
| North Europe (lreland) | Finland (europe-north1) | EU |
| Japan West (Osaka) | Japan Osaka (asia-northeast2) | ASIA |
| East US (Virginia) | South Carolina Moncks Corner (us-east1) | US |
| Southeast Asia (Singapore) | Singapore (asia-southeast1) | ASIA |
| Switzerland North (Zurich) | Switzerland Zurich (europe-west6) | EU |
| France Central (Paris) | France Paris (europe-west9) | EU |
| Korea Central (Seoul) | South Korea Seoul (asia-northeast3] | ASIA |
| United Arab Emirates (Dubai) | Dammam, Saudi Arabia (ME-CENTRAL2) | ASIA |
If you signed up to AvePoint Online Services with the data center North Europe (Ireland), Australia Southeast (Victoria), or Germany West Central (Frankfurt), and you have purchased a subscription to use AvePoint Azure storage to store backup data, the following storage regions will be available for selection when you sign into the Cloud Backup for IaaS + PaaS interface for the first time:
If you enable the Availability Paired Region, it will be implemented through the Azure Geo- redundant storage functionality. For more details, refer to this . The specific secondary region paired to your primary region is determined by Azure; you can find this mapping in the official .
*Note: The Availability Paired Region is not available for data region.
| Data Center You Signed Up for AOS | Available Storage Region for Cloud Backup for IaaS + PaaS |
|---|---|
| North Europe (Ireland) | North Europe (Ireland)Qatar Central (Doha) |
| Australia Southeast (Victoria) | Australia Southeast (Victoria)New Zealand North (Auckland) |
| Germany West Central (Frankfurt) | Germany West Central (Frankfurt) |
| United Arab Emirates (Dubai) | United Arab Emirates (Dubai) |
Before you provide your storage information to the Cloud Backup interface, you must first add the AvePoint IP addresses to your storage firewall or configure the firewall to allow AvePoint servers running on a dedicated ARM Vnet subnet to access your storage location. For details, refer to Allow AvePoint Agent Servers to Access Your Storage Account.
Once you save the storage location for a specific region in a backup scope, you can no longer update the storage for that region in that scope.
The snapshots for managed disks created by Cloud Backup for IaaS + PaaS will have the following tags: CreateBy: ACBVM_{tenantId}; JobId: {FB or IB}{Date&TimeStamp}; VMName: {VMName}. You can use these tags to filter and manage the snapshots created by Cloud Backup for IaaS + PaaS.
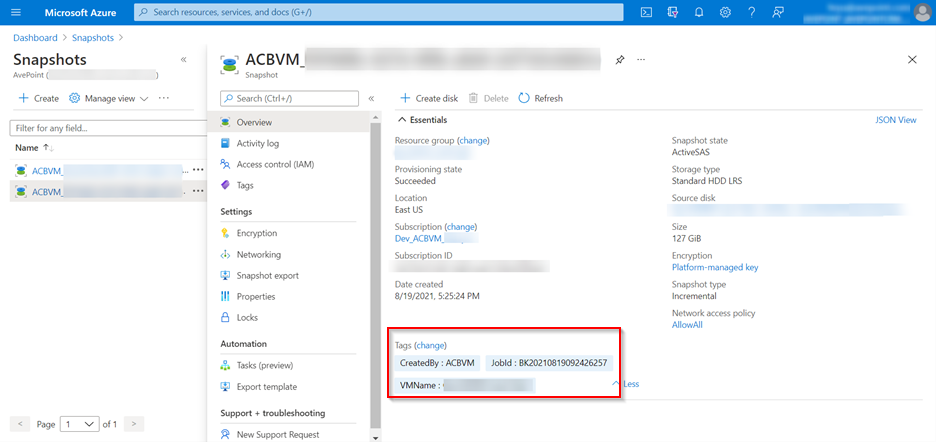
Backup Retention
The data retention settings can be applied to your backup data to help save your storage costs. You can configure a custom retention period for your backup data up to the retention policy in your subscription.
Once there is backup data of a backup scope approaching the retention period, your tenant owner will receive the Data Retention Notification. Once the next full snapshot of your backup scope takes place, we will begin pruning the old backup data that met your retention settings. Your subscription capacity will be released after the backup data is deleted.
Data Restore and Export
The Restore page allows you to browse the recovery points of each service type to find the data that you want to restore.
For Microsoft Entra ID and Admin Portal Settings, you can also use the Compare method to generate a comparison report for the backup data of a specific recovery point against the Azure production data to help you easily locate the changes that you may want to revert. Note that if the properties that you have updated for the user or group are currently not supported by Cloud Backup for IaaS + PaaS, the user or group will be tagged as Modified in the report, though the report cannot show the differences.
After you have found the data at a specific recovery point that you want to restore, you can choose to restore the data to its original location or another destination. The data of specific types also supports being exported to a local location. A monthly export limitation of 500GB/Month has been applied to Azure VM and Azure Storage. Data cannot be exported once the limit has been reached.
Refer to the table below for the data types that you can restore and export or export only:
*Note: The data types protected by Cloud Backup for IaaS + PaaS that are not listed in the table below support being restored only. For the Azure VMs, Azure Storage, Microsoft Entra ID, and Amazon EC2 instances, you can choose to restore the backup data to their original location or another destination
| Data types | Restore & Export | Export Only |
|---|---|---|
| Microsoft Entra ID > Users | You can download the user properties with a script. You can use the script and the downloaded information to bulk import/update the users to a local directory. | / |
| All data types in Azure Storage | √ | / |
| Azure VMs & Disks | √ | / |
| Azure VMs > files | / | √ |
| Admin Portal Settings | √For the list of settings supported by restore or export, refer to Admin Portal Settings. | / |
| All data types in AWS Platform Configurations (Private preview) | / | √ |
Activity and System Auditor
Using the backup statistics of Microsoft Entra ID, Azure VM, Amazon EC2, Google VM instance, Azure Storage, Admin Portal Settings, Azure SQL, Azure DevOps, and Azure AD B2C on the Backup analysis page and the total used storage space on the Subscription page, you will get an overview of the scale of your resources being protected and the storage used for data protection. You can also check user activities on the System auditor page. For details, refer to Reports.
Through Job monitor, you can monitor job status and download job reports to get a better understanding of your backup scope and performance and take responsive actions. For details, refer to Generate and Download a Job Report.
Use Public APIs for Job Information
You can now use the Cloud Backup for IaaS + PaaS Public APIs to get the information of backup and restore jobs. For details, refer to Use Public APIs for Job Information.
Configure Date Format
You can configure the date format for the Cloud Backup for IaaS + PaaS environment and notification emails in AvePoint Online Services > Administration > General settings > Culture settings. For details, refer to .
AVA Chatbot
Click the chatbot icon in the upper-right corner of a page to chat with AVA (AvePoint’s virtual assistant). For any product-related questions, AVA is here to help.
Data Security and Management for Google
The multi-cloud security platform for Google, seamlessly integrates AvePoint’s data protection technologies into a robust and scalable solution. This platform empowers you to manage, govern, and protect Google Workspace and Cloud with confidence in the security and quality of your data.
These features collectively enhance the security, management, and efficiency of your Google Workspace and Cloud environments, ensuring robust data protection and streamlined operations.
